Data source
The article "Modern Internet attacks" is provided by Sophos Plc and SophosLabs.
August 2007
The Internet is a vast repository of information, requests to which (through the search engines) are an integral part of many people's working and private lives. Using Internet search engines to identify potential targets is especially important if the attack aims at the web resource, whether it is a site or a separate web application. This technique is used in a number of malware instances, the most famous is a Perl/Santy [27] — a worm that relies on Google search engine to identify new victims who use a certain Internet application for forums. Before hackers used special secret tools to find vulnerable computers in the network. Now it is possible to find suitable targets using the search engines. Imagine that a vulnerability is found in a popular forum and blog application. Attackers can use search engines to identify the sites that have pages created with this application. Then they create a list of potential victims.
The massive use of the Internet search engines allows the malware creators to expand the range of their action. Creating sites that have high ranking and are listed in the top search results increases the chances that a victim visits such a site and becomes infected. Often it becomes obvious that the content of the compromised page was changed to manipulate the search ranking. It is very common to see several blocks of links to pornographic or pharmaceutical sites (see Figure 6). To keep them invisible, the "style=display:none" attribute is used in the blocks on the page. This phenomenon is called link bombing (or Google bombing [28], despite the fact that this method is also applicable to other search engines). The site is filled with lots of links to another destination site, to raise the ranking of the latter in the search results. Earlier this year, Google started to combat this phenomenon with technologies that can minimize the consequences of such manipulation with ranking [29].
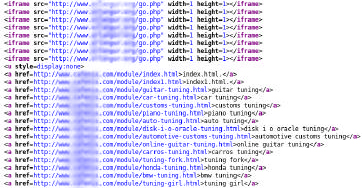
Fig. 6. A fragment of the source code added to the normal site during the attack. You can see the added iframe tags and the "bomb links" blocks.