Encryption with a master password
Security of the encryption key
The security of the encryption key is of primary concern for password protection. If an attacker discovers this key, it's easy to hack the entire password database, regardless of how sophisticated the encryption algorithm is. Therefore, the security of the EncKey is based on the following principles:
- EncKey is encrypted with the asymmetrical RSA-OAEP algorithm.
- In order for the browser to decrypt the EncKey , the user must enter the master password. The master password is known only to the owner of the passwords. It is not saved on the computer, so it can't be stolen from it. Immediately after decryption of the EncKey, the entered master password is deleted from the computer's memory.
- The EncKey is not mathematically associated with the master password. This means that the resistance of EncKey to brute force attacks is constant (matching a random 256-bit number) and does not depend on the complexity of the master password (the length, use of dictionary words, or character set).
Advantages of encryption with a master password
Encryption with a master password gives users the following benefits:
- An outsider who gets access to the computer will not be able to use the passwords.
- Loss or theft of the password database does not mean that all the passwords must be changed immediately.
- Neither Yandex nor anyone else will be able to access the passwords during syncing.
- Passwords in storage are more secure. Even if malware can steal the encryption key, it can't use it, because access to the key is locked by the master password.
Note
If the user has a master password, they can force changing the encryption password and re-encrypt all the passwords in the database. To do this, the user just needs to disable and re-enable the master password.
Steps for encryption with a master password
Encrypting the key and the password store
How the key and passwords are encrypted in storage
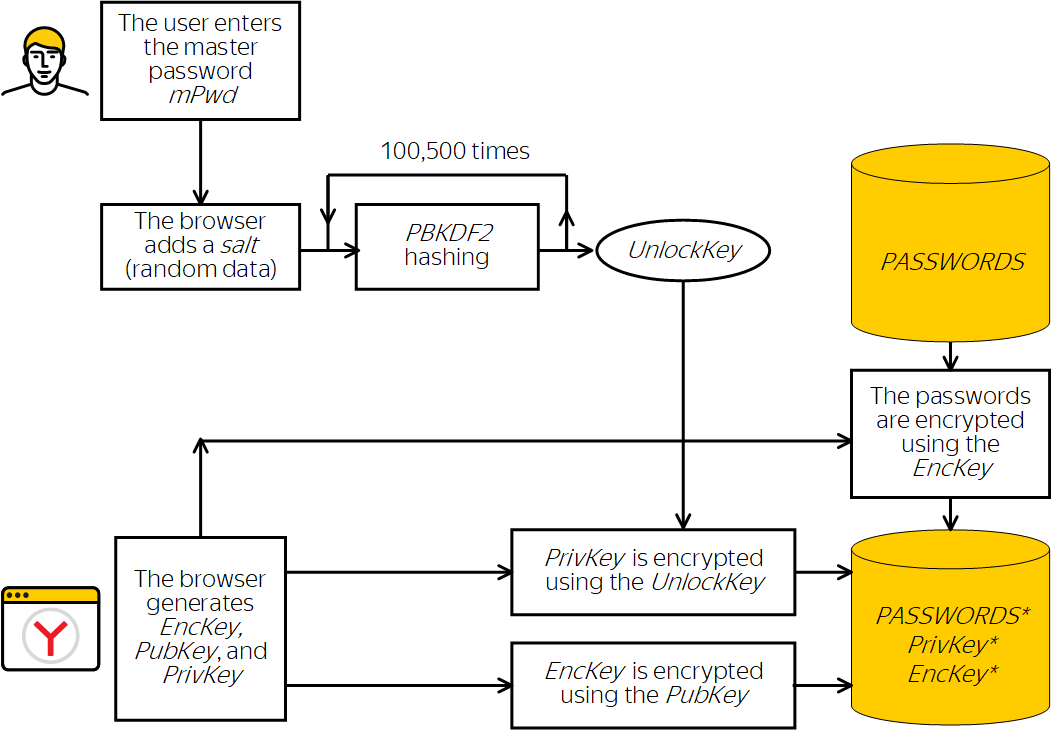
-
The user initiates the creation of a master password.
-
The browser uses the OS random number generator to create a 256-bit EncKey.
-
For the EncKey, the browser generates a random key_id that is not mathematically associated with the EncKey. The key_id is stored in every entry in the password database. If the user enables password encryption on multiple unsynced devices, they might end up with several different EncKey keys. When syncing and combining the passwords, key_id makes it clear what is encrypted by which key.
-
The browser uses the EncKey to encrypt passwords with the symmetric AES-256 algorithm in GCM mode. The same key is used for decrypting the passwords from the storage.
-
For cryptographically secure protection of the EncKey, the RSA-OAEP asymmetric encryption algorithm is used. To do this, the browser generates a key pair: public (PubKey) and private (PrivKey). The EncKey is encrypted using the public key, and can only be decrypted using the private key (PrivKey).
Note
Because the public key is used for encryption, the browser can:
- Change the master password without changing the EncKey.
- Create a copy of the PrivKey with a different passphrase and use it for backup access to the storage.
- Add passwords to the database without asking for the master password (for example, when syncing encrypted password storage with unencrypted storage, the unencrypted passwords can be encrypted using an additional generated EncKey1 key).
-
To protect the PrivKey from unauthorized use, it is encrypted with a passphrase using AES-256-GCM.
-
The UnlockKey is used as the passphrase. To make this key cryptographically secure, the browser generates it from the master password, the key_id, and a salt with multiple hashing:
As a result, the master password chosen by the user is transformed into the 256-bit UnlockKey. The resources required to hack this key are comparable to the resources needed to hack the EncKey.
Note
The field of crypto analysis continues to develop, and researchers are discovering faster ways to crack hashes. This is why the browser's hashing mechanism is not tied to a specific hardcoded function. If necessary, we can easily replace PBKDF2 with a more cryptographically secure function.
Example of EncKey protection with a master password
Public EncKey:
Mh6lu1xRuZFo/qJ2yktfJch2nAzlgY4+OPADyLQYfrkbR0hxae9M5nVdafthJa2QHG18sZbf2VOxveH87naRb3vq3oJykfxlVHX4bllYDCcLISzHZVnxF2yMM0r4BXl8Uq+nuINiWx8kaKtrULrdwnMGU6eOuOLZvv/wLDzQvz74iuQUgoR3NSpOByFnY/BkAmGWbQ5KXTYqqIcrcqkG1xb3EAQGEG8KGPtQsTvLsHL1QdjteMZ9CBBLAWjYd/kdrZsx+MU96XMEA+ViBU0ot35cAPVBeWgAyMZhvM9sYy4zB2HrCg+n14kSc85OjNEqAChQDeHVtcbBfyshnKB0Qg==
Public PubKey:
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAyiZMYsF3r121EAqq9spGWDife8bUEr6eyAEP3ip2gm6KaNzkyPGiDXN0zIidMjHKBzxjymtyQyY29DM26w1DQUK6Bd8aNvPXayscHXOKkId7L7+D1qc3mm9FJ/03Yi+pOa4yxVItgUZs9kpyW2LI9begHn62n0d6khsu6A2Iws66rohSXjPo6J2zONpWVn/YNz4o8QyB4O12msEB2Uf+NSFJjqNFAMUmGdTfcpUZ5Qz6Q7V0i5CRgONn2GeqqEaHwa+judPGxrcL1QK3QZGhXChmzwGMAySdVWkwMbQxBMSKMRLbRhM0D19W00TdwYAMLbmX/E8Ekthx1L3WCK7Y1wIDAQAB
EncKey* encrypted by the public key:
VlZecAIaRweK2+ZnTAZzKskONjMGqqGWTli0Shr0zFcIQJwNaUSDTdflbSDEdR2KGh5HcShmRRaciQG0A59f8aBlYkoMEqLW+7Hoo1CJsunAxDioSoLf3YlpdfGto5
HFXsuoH1OcRTsKh/yCPiW9FTQrdPTIpLwnQjRi4nDkVLft3aWDlqvqcCHd4EKDTwioTIlhaUGBbfNDP5bQlt+KTl+cdOAQcOv4c1pJhN0hA2G93kLK32zcHIMYf89wmBnP1/leorp38W+hsZcpSJvhV2lufIZ74G0mMA6zBNYOYU/NLss7GpecwAZGcL5rlPbGGATBIoxa9S1QC
1azjI3llQ==
Private PrivKey:
MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQCu6h5dF90Ow7zwFE8KDbspsIbiAnlJJVdWE6BBSk9ecUnvlSeNZe/whbnvAkNF7o9wYstAdKUrKK3T+IJmgvhERgM
QoYlQZQmxm2EP9gsG84h0nWCVL82Sl1CA86Bt2Cr05UHGH9kWMC/FB7coPrURqXbMPtM0cwtWoIqzJJ6+EWkR/ucq8Bbrm9wnK1R3vFGXsFlTLWVmHEyY83gVnqwRR2u70b32j9qM91XevcRqWOYLNLIzio3FHTHuThsyy1cLYJsHPhc6ATqAKtYGcfWN4YPcIW7CG5uB3hFKi/
xGgOYxR38Ursw88rJqn1Od0QFpPLUxoPmXgydNYYIvE0iVAgMBAAECggEADWLWawpx/PjG41qyh9LwMWsUj4Rf8tScP/ali4mb1F74KRExozUbbT1Wsu9p5ZaxvIibBHZI06o7z16T4DOCu3reLi4mm5P373M0NOwAAQqvNTl8FD7BzUeuPggnDXD/LJnE9FwomXWbmkkSX86Yv
d7JvCzMrhVl1z3XD4msamA7VV/NdivL0Mn5cq5F2KGPLxqbH/nLCgxq4/Z0nAWIFJfGCx8C8sRALv2g7qK5PJVQ4VEttLpF6Qco31AwQQ0S2sWer+0y7m+GfZ+1tfdCE6ceZuEt4UsgF7q5at7lBfGHDdmH0F+sOYn+6+szJBPDLUFpO5d6udKGAiJZog23CwKBgQDWoJyFi/iQ
9ww2GzSanRDehNTLvNFqnDMGkrVNwAHhQ1FgXKDeW38ELPHQn21yt4GYzql/yHhS823ce7zLkHvKOcCfHWwHFfJimKqp2Rdp9MU6bU6WgZCNDkTr+AvNpyQ1FmiO/gc6qyB93fe+2RvHHZJ0YXuSG4XDbbQ45rsoKwKBgQDQocPUFV7iLvawmr3qRa8Bn/+0WXHzzdf5Nm8i4iy
faaVdrpvuFl9eIkVGjfYO65jHA+93oru7gWsLg9EPDdBBuADWf1PlIZw1EsykPnRLMBuLQFiPmHZdZSMhNWQWy1T8EOnTsEp9KujerQ9Yk3Uhvln3DrzuWMilqJWj6YQyPwKBgQC9TXRApjBbTEtM/bnsFVTnrykxeh0LdzHaPlQDe7MsyH9iCtEoznK9cBbo93VFlW2NJdqCho
L6RxNDQTBIK+vDdiTbMswxg74CEL2WiZAJOIcs/XQvc5/XihpoNqPSg/V/jYAzfwNJT96cpcb6YewKN58RX1nqiLP2pzAqb/freQKBgCsFUGZJSdmGKaRdJFBMsju5jHbaAt9tUN241c3xqZXtqQXaXZkIz/2PP42+9EA7YLOZIiYfTmrp0vL66X8bMBh9It8YPmp/NcDT8ZLkt
gJTFzrtt9VUcQPtOQM+CTeSEiIwMqdOMO4CjSZttT5kmcCticuiJF9Zu3Y9fy3flzztAoGAMsTJRcyRe0qi0Z4nfpQkND6zPCUiTZwgvb51jQxapgWcR1NYRM0oAocqgftHGPXkxMUz+g08Mg+nzL4Vh8R6UQZE+k1LLOnLWpqRb9I23/hqudld5MJYq5e1tOJ8cwcJ+k6YRxN+
4qpW2qvQSH2g/rh+ynkHeQHxl9OAuRYTYNg=
Master password:
password
Salt:
/4dMZgU3GG5WfXMjYQbGNzKGxa/7RNFej43Nwx4mpws=
The UnlockKey, which is the passphrase for the PrivKey:
UfaND0ks2hulRHkLMGL9Zkpiu1gKBYJdYsqCVTnOIvs=
The PrivKey* that was encrypted using the UnlockKey:
NphBZAm4mu2h4FoS21D6H6MNWxsk2YlD0+JbQQ2S2ujzgQpgF/lq52VU8OT039naB6MQRNxbGRL7G8w+W7MFonMq3bj2pzNTi6qQPqmZmTm1hXp8cFgcBABpZtgBjqY5K
n93WfdIkUCHOR6TscHXD8tnYC5SvVkCr6dsx4XmghoIk3CFr9Fn1ujCvnbVF8z6jjsvSjZcXKU8KluHlxqWiZQEq1k0xohXWq+D/7WH9qGHdgTqgFt35tPCpwcFsDHdXdQ0GoVY6n09xazA9pgvy6xE8QvmwcotV+LAoS6eLdiaQ1h4moymSc3Vrvgk/CQ3SvtTwVqV7Hogv1FT
XOApvlFgVqVnP4i89wFbaR2+oElsa8RwI590DeYP+h9610SCYCPE+1npN4lme1EX3lFh9Ejkmm7KXcH0aw7T1u1UTVUixg/RZv5eYkfSx08I42v6tBSKJUA/5sgJpE3adXgMgggzJonvYDS+oYsGNL2EeCLsLBeKLMGz6cDYbalJFG+wxYYptoN1433GxHvEWtKiXuSbeF+hbrc
kzN+0MujZlEQ20IvgbkbK2ocZbDS7oHySQvc2tT6gIhaXRR021SM127ALmI95lSWIK/rvFJ8LNP5pqyFwval0ushXGURxSzuVfnoBFQjwoPqWY4GUIfebGnC92cZjy4nqloEFDTC0FeKI+zjPkuOXIos+UfTAufaqilw1QSQkTccWh5e2o1w7hEPXx0OyOldXGULvDMDqEncST+
UCOkPSlkRlBuNlqqQ0EDKcDobDATbkiM/i5tTq/kkeYcJkUPXNbvENVRi/0otCJ/nSHK+01Ea0yGavBMy1kc/LDFykC4o3xLiqApsB+9ZveMND0DUY6Ju5/dCWiAUoOO5igXOREJQywmZ13TOfc77b/Bc2z0v9puDon51+9NXlKc1fCde05jsMUAQ98P71hA8XpmpdBG8V9fnBd
NZr6aDjkqspEEeY44kc62/ocqtStQA3m7LHTcOypkgOjoZU1MFtXJE1eAibBC42eK0eufOWfvs31O2VnJNS1WNEoyPFbvumIg9QAR4jDeJKfMiIjHZw0HCubs6LRzH4KLSAIiM7yF6FtU+gfa81VoN+/bA3y6jGlAANf6rL8j89e/SMZSbB0i7s7qZLDUqRyFzcKWsClKObttMY
GPXR+w3m+BKr8APdZbrcGpyQOpR26+dZY+jxpa71Y55w3UwKVP50Df4VVo+ZWfHXI5Z0WW4XDfNe/cRp9aqBYlcCOT2dE67VjOgwVDYES7qiVe6g/fVNg6fLlr/44tqDhOF0Ty79T4URZrCnZPFgP+U4HR51o/v2c1sTIF/ON/FptgVgnKoNNIuFt6YCeEZ4sgd/zo83TkQuTd/
8RyCTof5aDpIlDkbEK+G/5e2vToze+PwvY30qV/EKk5GumoZsOvHzAl1dQpsJsINjN9aXcu7lJ+qH4e3M9VMCY5Ajlov5m3ni9tCnT/yF0il0tbOSQAESw/x/ZgsR2efvMfiGxX2KZ559nrOkk6RwKkkD/rl/hCarZ6rkAfbiuWl1Jl6g+mr+QIOPV+lV62VLagxQXLrjTuV05P
/8L8dVIEvyxa+vWZ6zoX5q4b0oJHglf+viGa2t18LugZ4lBU6djwNFNQJ08DYN9ttYAqY2gUN84b1HEr9Dp8rDIAg=
Storing a site password
Flow for encrypting a new password
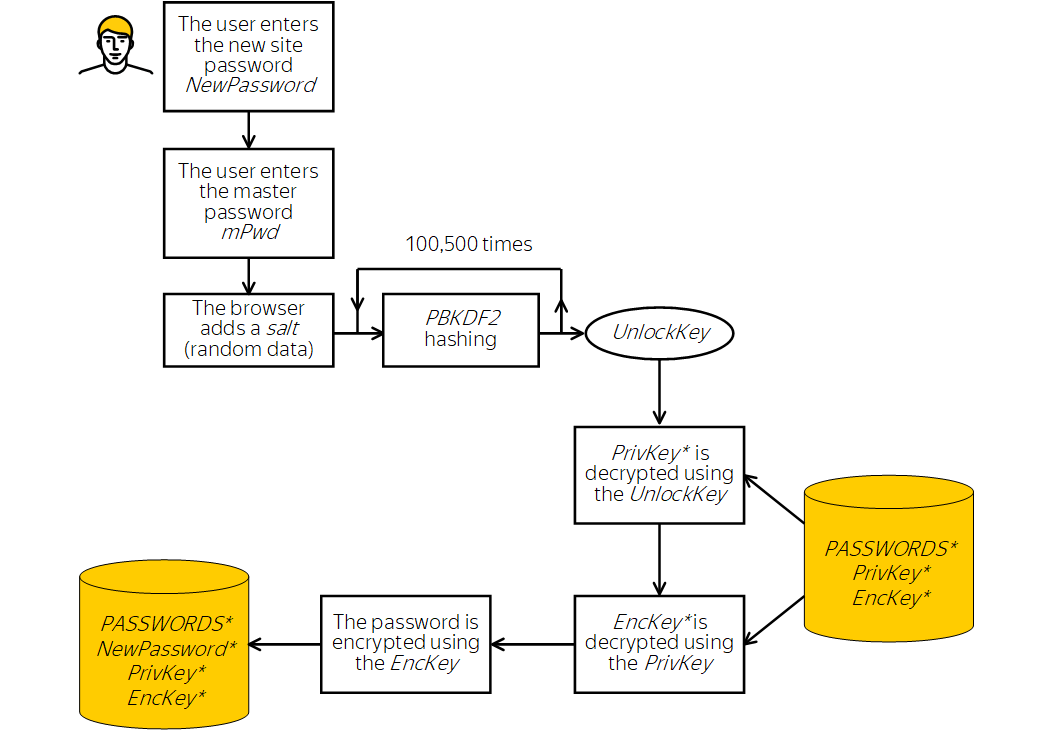
If the user needs to save a new site password, the browser decrypts the EncKey, uses it to encrypt the new password, and sends the encrypted password to the password database.
To save the password in the database:
- The user must save a new password.
- The browser requests the master password (mPwd) from the user and generates the UnlockKey.
- The browser uses the UnlockKey to retrieve the PrivKey.
- The browser uses the PrivKey to decrypt the EncKey.
- The browser uses the EncKey to encrypt the password and send it to the storage. After this, the master password and the password entered by the user are deleted from the computer's memory.
Password decryption
Flow for decrypting a password
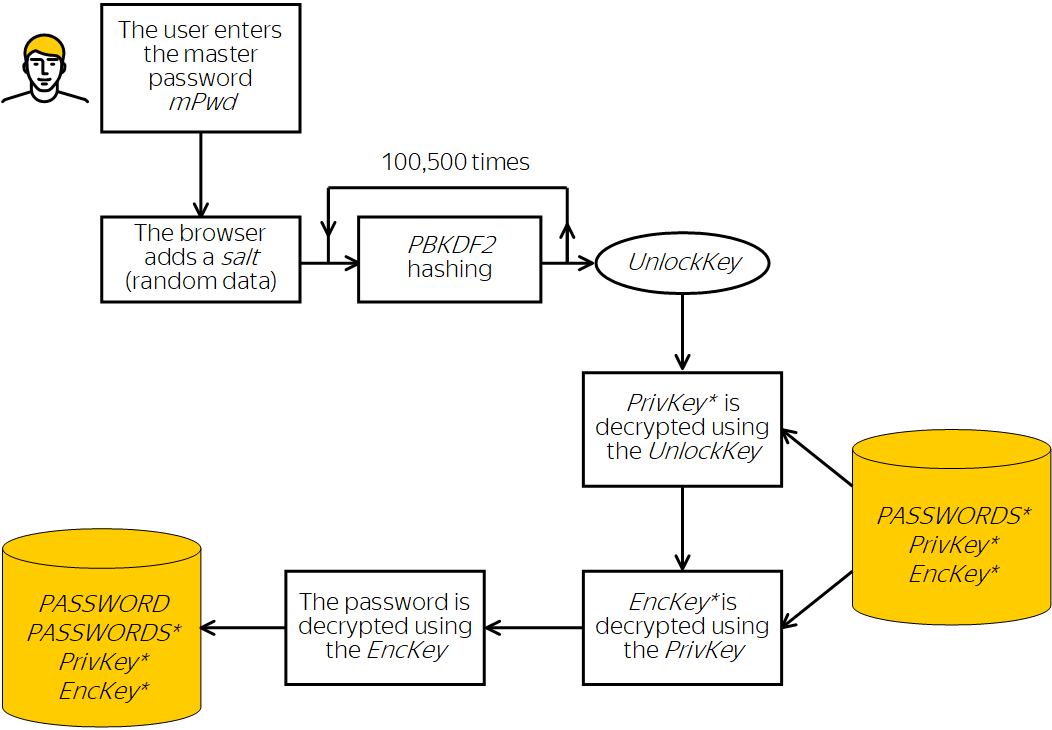
The EncKey is decrypted when the user needs to:
- Enter the password in a form on a site for authorization or to change the password.
- Open the password manager.
To get access to the password storage:
- The browser requests the master password (mPwd) from the user and generates the UnlockKey.
- The browser uses the UnlockKey to retrieve the PrivKey.
- The browser uses the PrivKey to decrypt the EncKey.
- The browser uses the EncKey to decrypt the password.
When you fill in an authorization form, the browser decrypts the password and inserts it into the form. Then it deletes the decrypted password from the computer's memory.
Changing the master password
Flow for changing the master password
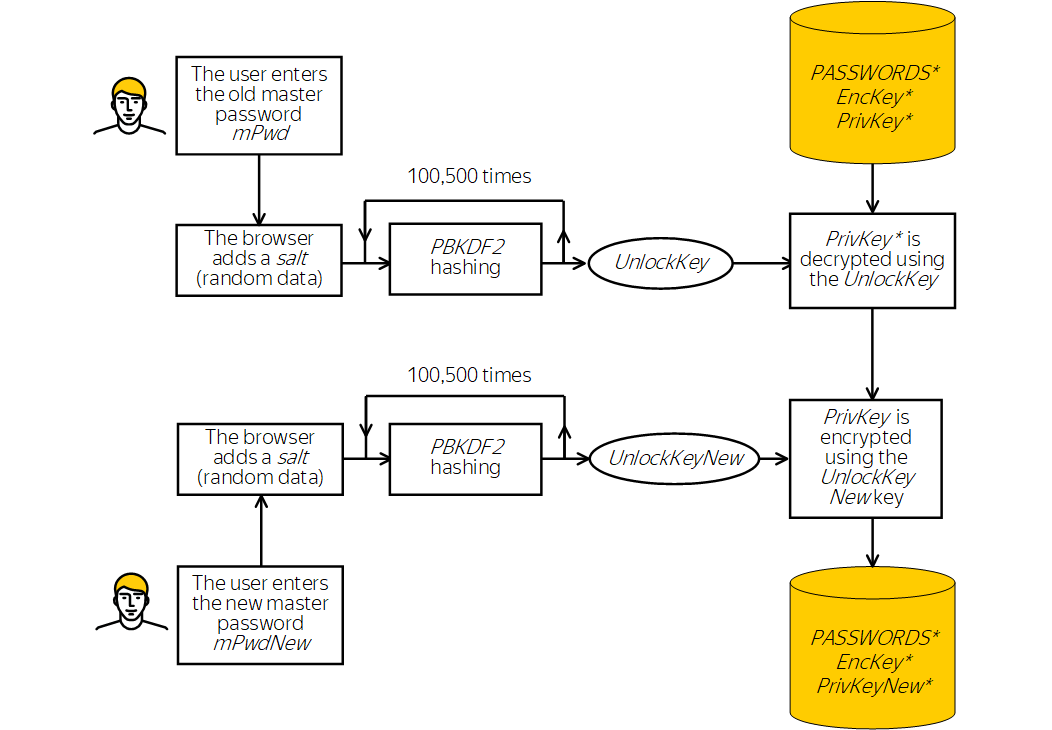
The EncKey is not mathematically associated with the master password, so to change the master password, just change the UnlockKey passphrase that locks the PrivKey. The EncKey doesn't need to be changed.
Note
There is no technical reason that prevents generating a new EncKey, but it's inadvisable. By changing only the UnlockKey, we avoid the difficult, risky and lengthy process of re-encrypting the entire password database, which would be inevitable if we changed the EncKey.
More information
- The browser prompts the user for the current master password (mPwd) and generates the UnlockKey.
- The browser uses the UnlockKey to decrypt the PrivKey.
- The browser asks the user for a new master password (mPwdNew).
- The browser uses the new master password (mPwdNew) to generate a new key (UnlockKeyNew) and uses it to re-encrypt the PrivKey.
Creating a recovery key
Flow for creating a recovery key
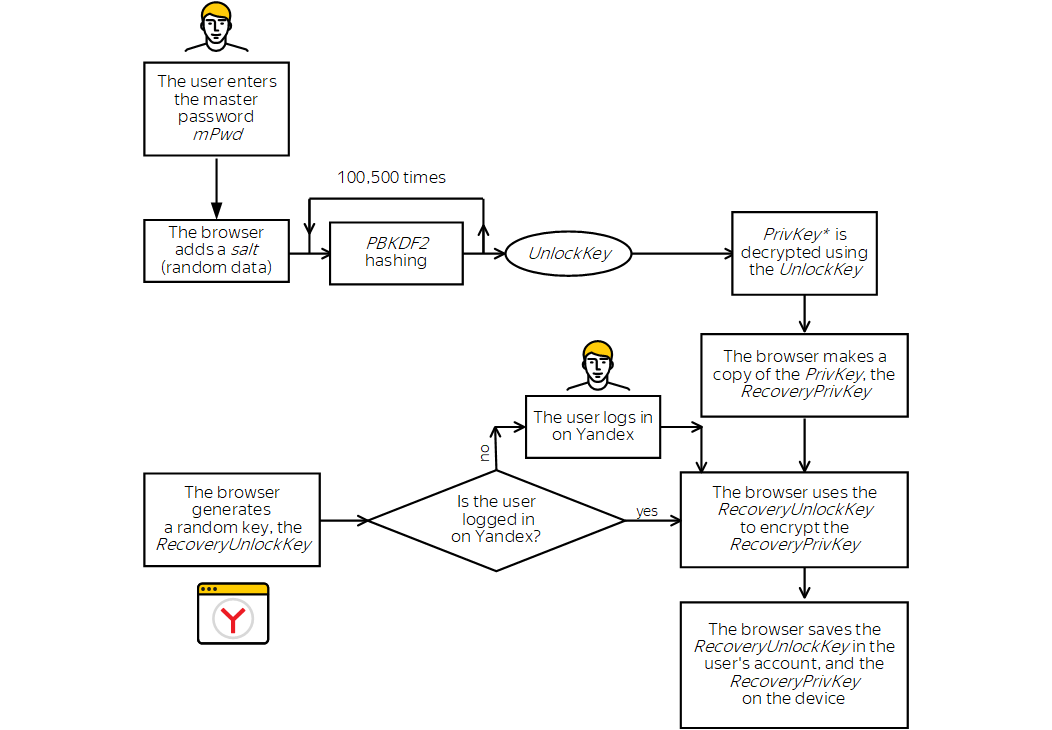
- Why the recovery key is necessary
-
The user might forget the master password. In this case, you need a way to restore access to the password store, but in a way that is not available to anyone except the user.
The master password is only needed to decrypt the PrivKey, so to access the password store, it's enough to have a copy of the private key. The task of restoring the master password is simply a matter of securely storing a copy of the PrivKey.
The recovery key (RecoveryPrivKey) is the copy of the private key. Some password protection systems offer the user to print out the recovery key (or QR code). We don't consider this approach to be secure enough, because the printout could be stolen or lost.
Our solution is to encrypt the recovery key, store it on your device, and store the decryption key (RecoveryUnlockKey) separately from it on the Yandex server. In order to get the key from the server, the user must verify their identity by manually entering the password to their Yandex account.
Storing the recovery key and password separately means that the master password can be reset without introducing additional vulnerabilities. If the user forgot the master password, they can request the password from the recovery copy of the private key. The browser decrypts the RecoveryPrivKey and then encrypts it with a new master password invented by the user. Access to the password store is restored without having to change the EncKey and re-encrypt passwords.
Stages of creating the recovery key
- The user agrees to create a key for resetting the master password.
- The browser requests the master password (mPwd) from the user and generates the UnlockKey.
- The browser uses the UnlockKey to decrypt the PrivKey.
- If the user is not logged in on Yandex, the browser asks them to log in.
- The browser generates a random 256-bit key (RecoveryUnlockKey) and saves it in the user's account on Yandex.
- The browser generates the RecoveryPrivKey. To do this, it makes a copy of the decrypted PrivKey and encrypts it using the RecoveryUnlockKey as a passphrase.
- The browser stores the RecoveryPrivKey in the browser profile on the device. In the future, this key is stored only on the user's device and is not uploaded to Yandex servers during synchronization.
- To enable the user to recover access to passwords from other devices, the browser sends the EncryptedRecoveryPrivKey to all the user's devices during synchronization. This is a copy of the RecoveryPrivKey that is encrypted with the UnlockKey.
- As soon as the user syncs another device with the Yandex server, the EncryptedRecoveryPrivKey is sent to this device and stored there in encrypted form.
- When the user enters the master password (mPwd) on another device for the first time after syncing, the additional encryption is removed from the EncryptedRecoveryPrivKey. It is transformed to the RecoveryPrivKey, which is protected by the RecoveryUnlockKey.
- The RecoveryPrivKey is stored on the device and never synced in unencrypted form. The user can use it to reset the old master password and create a new one after getting the RecoveryUnlockKey from the account.
Example of generating a recovery key
Original private key (PrivKey):
MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQCu6h5dF90Ow7zwFE8KDbspsIbiAnlJJVdWE6BBSk9ecUnvlSeNZe/whbnvAkNF7o9wYstAdKUrKK3T+IJmgvhERgM
QoYlQZQmxm2EP9gsG84h0nWCVL82Sl1CA86Bt2Cr05UHGH9kWMC/FB7coPrURqXbMPtM0cwtWoIqzJJ6+EWkR/ucq8Bbrm9wnK1R3vFGXsFlTLWVmHEyY83gVnqwRR2u70b32j9qM91XevcRqWOYLNLIzio3FHTHuThsyy1cLYJsHPhc6ATqAKtYGcfWN4YPcIW7CG5uB3hFKi/
xGgOYxR38Ursw88rJqn1Od0QFpPLUxoPmXgydNYYIvE0iVAgMBAAECggEADWLWawpx/PjG41qyh9LwMWsUj4Rf8tScP/ali4mb1F74KRExozUbbT1Wsu9p5ZaxvIibBHZI06o7z16T4DOCu3reLi4mm5P373M0NOwAAQqvNTl8FD7BzUeuPggnDXD/LJnE9FwomXWbmkkSX86Yv
d7JvCzMrhVl1z3XD4msamA7VV/NdivL0Mn5cq5F2KGPLxqbH/nLCgxq4/Z0nAWIFJfGCx8C8sRALv2g7qK5PJVQ4VEttLpF6Qco31AwQQ0S2sWer+0y7m+GfZ+1tfdCE6ceZuEt4UsgF7q5at7lBfGHDdmH0F+sOYn+6+szJBPDLUFpO5d6udKGAiJZog23CwKBgQDWoJyFi/iQ
9ww2GzSanRDehNTLvNFqnDMGkrVNwAHhQ1FgXKDeW38ELPHQn21yt4GYzql/yHhS823ce7zLkHvKOcCfHWwHFfJimKqp2Rdp9MU6bU6WgZCNDkTr+AvNpyQ1FmiO/gc6qyB93fe+2RvHHZJ0YXuSG4XDbbQ45rsoKwKBgQDQocPUFV7iLvawmr3qRa8Bn/+0WXHzzdf5Nm8i4iy
faaVdrpvuFl9eIkVGjfYO65jHA+93oru7gWsLg9EPDdBBuADWf1PlIZw1EsykPnRLMBuLQFiPmHZdZSMhNWQWy1T8EOnTsEp9KujerQ9Yk3Uhvln3DrzuWMilqJWj6YQyPwKBgQC9TXRApjBbTEtM/bnsFVTnrykxeh0LdzHaPlQDe7MsyH9iCtEoznK9cBbo93VFlW2NJdqCho
L6RxNDQTBIK+vDdiTbMswxg74CEL2WiZAJOIcs/XQvc5/XihpoNqPSg/V/jYAzfwNJT96cpcb6YewKN58RX1nqiLP2pzAqb/freQKBgCsFUGZJSdmGKaRdJFBMsju5jHbaAt9tUN241c3xqZXtqQXaXZkIz/2PP42+9EA7YLOZIiYfTmrp0vL66X8bMBh9It8YPmp/NcDT8ZLkt
gJTFzrtt9VUcQPtOQM+CTeSEiIwMqdOMO4CjSZttT5kmcCticuiJF9Zu3Y9fy3flzztAoGAMsTJRcyRe0qi0Z4nfpQkND6zPCUiTZwgvb51jQxapgWcR1NYRM0oAocqgftHGPXkxMUz+g08Mg+nzL4Vh8R6UQZE+k1LLOnLWpqRb9I23/hqudld5MJYq5e1tOJ8cwcJ+k6YRxN+
4qpW2qvQSH2g/rh+ynkHeQHxl9OAuRYTYNg=
Recovery key (RecoveryUnlockKey):
d84eaaa2d1a44d7716b59129c9b48b0339b97eb3d3e28405a6e212b8fc82535c
Copy of the private key (RecoveryPrivKey), encrypted by the RecoveryUnlockKey:
NJdSM0ZBf4IbLCcZIcCex/ul3UxkOVdl+05WyRg9yLwP97EKMzy4yMXvLLiq27H/xxfzkAs7DaYWSTqNyW/iGIidpUcyMKffM+P2i4vSjngTpVMQQl0ISQ1P2+Ym5dsUOtMHNh5SPQOVvcgZ0Nvq4GVVMVoX6HlnLsK3EmwBOmlMuuWhHbMPRaiJl4xCRZlmTQlRNbhSQEGNHkcDTPKUG4Li35OSKnZRO2WVUfdgNJeUtUWWncoSLwnxzBqdCvYzdicn0DtagI0aNOoXZgM1gCCfiwIJH5TcrAMELGxbjXo+74hjJ3QdhUqzsHTnghOxp+R8oU6ReGT84J1vhlkhwBX9/kkX+7GPKnJHWt2jASdTxmdf27AA34/e+TeVThPyMQWlVG9GTptzrGjsoAomvWKcJmUJwGlUNytqe9c47iKyeqruzdtvntPeZi5BKmfRdIXjzsmtAnUftLjGLF990t3vmSN0VUrXBNVWsMycvBvAsyOhHjHLfJbHDfKFOgJouBWruHRblpDiWBYlrH/Q4yyEAHb/tDUANu4p3D6sySI8WHLCGXVvXT3V2qbDs82kFETZYwwe6m7T2bjNToh4Vp04KzWCeaq9MMWk0nRIkXogZFN0QzM5Fdm8LMCmecFggGEbcIIdH3hdgqmhmhj8beU6WmxinFOVAGTJg+TnLWPDoFaAI/BHVDUjpICu4iY5jjO4IVwrDqN/EeBC4e98xl+Oi0cXfkwlb+OAZMQBB6r2U5WvawcdLeQVb/GP7N8/n5f6FxVEYfN/jQhe3UNEy7u4QUSXg2o85geZXKJcchxIQ69qfi4sIYqfVqwKIeBl8pZB3L17ErhLaADuEnzWq2B3ZSZswd0HxHIpKYO42OuILEVMyqEMg7QYofTeywa8CReq/Dsd5Jhke7WP5/fAoy7dlfYtkvjQeXIEdL2x6j5ubYUo+dZQpnGJpU/klGJb4qhtVgjx33pEX5RelZNDStDCcUDxUsEluLCISOfsL81w/dunOVtksL9muvn786D1EkuoefGP1KBku8hYW8K19ysF+tD0LI1rEOr6stFFq4yCQUnC+fTex0/gWyrhEp3qEeeG/FHTy60P9vGQvmf0AOXz+Qm0pKB0W0qyHeusVd9EifhkcxMHRYAUWU1tPwDv1++yU6qKLdp7LtMKI1jdoVcH9Kl7oeFhlQpP5/vhXbWdROdaCpdJ41BB3/VfhhfhHqwkwRUZaM3JaquWoL0+TlRkqvd8THRIP5SmSC4w5UtjJKELnvU/WpCsUPjG3Ruqj/drs1uatOYTZJiaalMPP8UjBzdJ6Z5H7MYPiVH2Z7FqeXe+RGTWC9q+jbcGW7D2yjX7WAGh200GlR8jp64HAK/QVvnXyldUd98+BqqDNcct0BjFIXBQPfq4ee3MPyi9WLnFvVMTIEaQp/7KjDarwwUb4BDBmUUuVspMbj/7ijVWX/FT7HYHS+NcU+5t3LjFqoJfHUO4e9g5FpRc3eiIOS6BmZ8XI9zGIpjKOjDOoUcxSmeY06Fx22QUlSsDwGPvyq4bzs+4MNHNmxLjZgSCdh6QzjA4qv7gE0HKsBwh4xRJK8oidvC8kRL5i6h4sF5CyzY7W+mSUaa6nQ+jXlmm7Y8ApnTcFly4ybXWZvp+7lEhfHeZsoRUTdxgLjzaPMeAc+U=
EncryptedRecoveryPrivKey encrypted by the UnlockKey:
7oXPhdrujp/l/wEzBYRFC1ynD2AQATdSkOckzXwiRMeWB4czZjSEZ3u0ZWYy+Hinx80zupFS3A0n7fnzB0Ogs6h6SsMlD1WkImsZ3XaSf98u8VCVm7cILvOvNz5j2xzgFVBmQiyTbgf5NSIwsJte7Uz9p6Bb5fCRcV6sAzt13IdBSXJ6Xa11tUqiMZXn+JYzCzHyh7zAWXr41e9TaWv6mJ3EWw28OSgGD4eeLOxJ3UihzUaFYtlXmJkmUaVZcZwIOXua58FABJqu6IXIgC/Ssoq/biq6sepfVHY4xMgjkfb/KlJzZPjWkmBUJiHgvAibqQDK+lv/TtTwVRSoC4z80SjvnJ37Z4IFE40rSb84A30Va7iHGNeeJx4vqWV8oZJFEwyb9RbuQNICvNo5VkJx465N9d2Nb9iTJx+YhVLAmmtS4kyYk+7CMtIpH9+qM9cJHbgqpSpZ+kr/Go+ljlC0jbCaNVtZEvGMCLmNCGzhsLXbtCwM1zcIQcCvVPCI1jGGLi39P2UYa1pfh78FceCU7558DPiNDWk1VGBYbRBkZ2u1A5Oei+mUpSUdeMRi0jWp2F2SVMX7mzP9njOj6kqmEymgrjSpyA74Cfb2bkXi2nT9bhdOfYZxphBPj8346jZ38tACTLbWDmvbuMt09G8noaAeovZwefkuDzDNHuCz6XJ34nN/LiclmD7MxS5OHHGkfyyLyUhTe3TqjZanNp9bXvs2DVGKVBcY0Q5+Xpt+sNTBCPjZUqTsFOnu06Gj5PQGuOQHXcKWIzQF3vILG84lFF+Eg+5j/3c5YaCoPCzF2kkeqnGe7B/EPeEeEKNJ8ZOOvRWcdxDTHQhpu+SvT98V5X/8uJErqM+pA4FDZ5wOmUD0mSXR4pbv/geD2wlzeQV1AJs2nBR4356TBL9kLOxQu9pDcdsd45PniWzR9leqCYsILzVP8wSVh3gBl7o5fhRnz/YeyFkXF5FUc0hPUG9exAy83zir2i9G1d7DqDvYhYoHUd4lFrezz9p4TNy3QPJzH77fFnbCq7PbuLvbsdwjBzm/h4zab5TSJ2NE543rmo3R1JgNMm3HFbNm69Jj5VoFtODdyFMSnGIM3wqqaiPVAj6oMovCgvqvJ8HcspaLPCczUp+cMdb0HlIRiUKAuVrEqMg4kTs2Mzzu53Q3queeo3jnwWvnclGZnZf1p1uO89n6YBe7BWmFrgO4vtbiziUS1y09PdxBDeUibuzEFj1m8Tevkc9ET9IMtEYPF7M6fRCy7xU63jZDOwOZZSrYNqKVBPabSnRodgn9Mjznn/wDWrQEsdEz6paABZUq58AtGNO/pb5poF8CWmRIEtFn0n9/47kESTcoZM1ycgtGPiZEeNDF0/LndCAmLWiEPEUHuVBfzcyJSD8AJ5FYFJOdx8l7LsWeKIrwOJrMMWsLz5JAoj1pMfJe8P6kgr6+6SIvCDfKiKcJqUrIukUvM7p0TSkbC5Kjt9MskmIRY2UAGvIEYdXscpegSSPOFXPP6zfBbzRMoVSnr89dbDNjfN0qneGI2JLvtwlGKLe1oxodFY+hHE1L76Yz7KX9hfCFT+hDJs3HESzRcMVdIKoym7ikA1PGOn8ioqDFbvsDkNH0vgVtfvb/afH68/MnLPUGVpTkhJzGC478pOZ6tJdwp9ehK0ItqPZkV4UgTaR6oSH2LF/Gne488lACgXIVfdUA38vf
Resetting a forgotten master password
Flow for resetting the master password
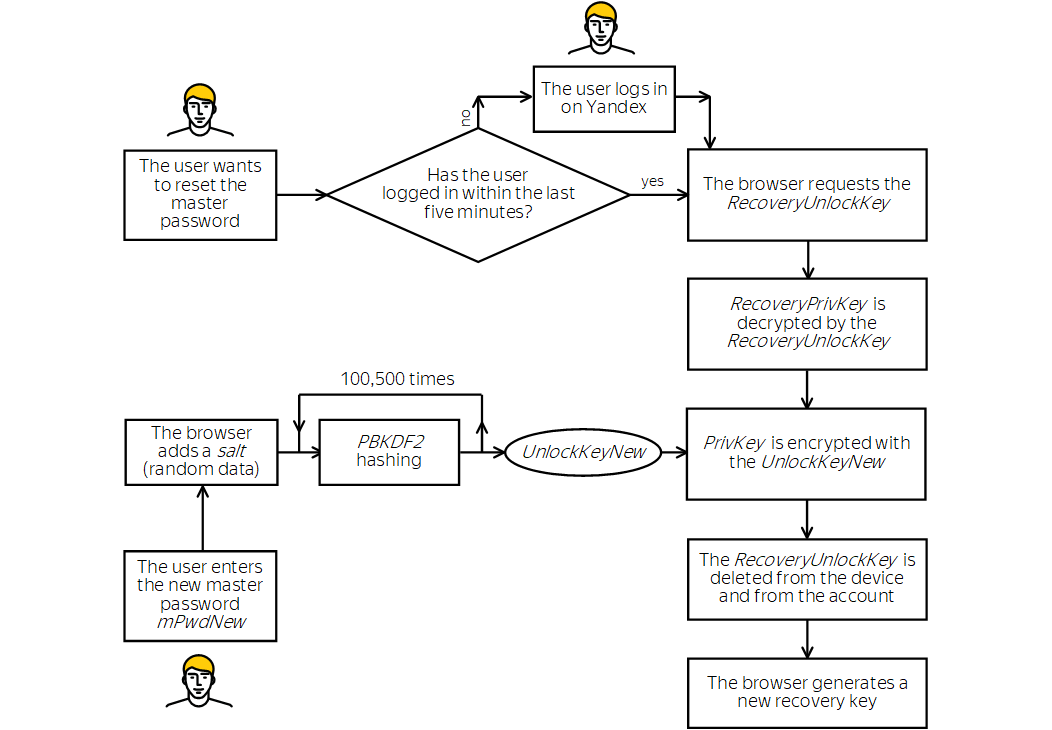
Alert
The user can reset the master password only if a recovery key was previously created. They can reset the master password either on the device where the recovery key was created, or on a device where a copy of the EncryptedRecoveryPrivKey was received after syncing and decrypted (in other words, the user successfully entered the master password on this device at least once after syncing).
-
The user initiates the master password reset.
-
The browser asks the user for a new master password (mPwdNew).
-
If the user is not logged in on Yandex or logged in more than five minutes ago, the browser asks them to confirm their identity by entering the password from the Yandex account. This prevents a situation when someone else could use the device to reset the master password in the user's absence.
Note
For this authorization, the password can't be inserted automatically. If the user does not remember the password from their Yandex account, they will not be able to reset the master password until they restore access to the account.
-
The browser asks Yandex.Passport for the RecoveryUnlockKey and gets it if authorization was successful.
-
The browser uses the RecoveryUnlockKey to decrypt the RecoveryPrivKey. Then the RecoveryUnlockKey is immediately deleted from the device's memory and from the user's account on Yandex.
-
The browser uses the new master password (mPwdNew) to re-encrypt the PrivKey and creates a new UnlockKey.
-
The browser generates a new recovery key (RecoveryPrivKeyNew) and sends it to the Yandex server.
Sync passwords
Syncing the password store
When a password store is synced that has the private part protected by a master password, the following are sent to the server:
- The encrypted EncKey.
- The public key (PubKey).
- The encrypted private key (PrivKey).
- The password store with the private part (passwords and notes) encrypted.
- The encrypted recovery key (EncryptedRecoveryPrivKey), if it was created.
Note
The UnlockKey is not sent to the server and is not stored on the computer. It is calculated each time the user enters the master password.
During the transfer from the device to the Yandex server and back, the data remains secure due to the following factors:
- The HTTPS protocol protects the data transmission overall.
- Use of GСM protects the public part of entries from substitution.
- The encryption used by the browser protects the private part of the password store.
- The encryption key is protected by a master password, so no one (not even Yandex) can decrypt it.
Therefore, Yandex servers store the addresses of websites and usernames on these sites in unencrypted form, but passwords, notes, and EncKey encryption keys are stored in encrypted format. Additionally, information necessary to decrypt it is not uploaded to Yandex servers.
Syncing the recovery key
The recovery key (RecoveryPrivKey) is created on the device and stored on it in encrypted form. This key can't be simply left on the device where it was created, because the user could lose the device and would not be able to restore access to passwords. Creating a recovery key on each device manually is also not a good solution, because the user might end up with a device where they forgot to create the key. Transmitting the key to other devices via synchronization isn't safe, because the password for the key is stored on the Yandex server.
To solve all these problems, additional encryption is applied to the RecoveryPrivKey with the UnlockKey. Decrypting the UnlockKey requires the master password, which isn't stored anywhere, so the resulting EncryptedRecoveryPrivKey can be safely synced.
After synchronization, the additional encryption is removed on each synced device when the master password is first entered correctly with the EncryptedRecoveryPrivKey. The restored RecoveryPrivKey remains encrypted by the RecoveryUnlockKey. The latter is stored in the user's account on Yandex and can be obtained only after the user manually enters the account password. A copy of the RecoveryPrivKey is stored in the browser profile on the device.
In this way, the user can restore the master password from any synced device if they entered the master password on the device at least once after synchronization. However, the recovery key remains secure during transmission over the network.
Stages of encrypting the recovery key during synchronization
- The browser creates a copy of the RecoveryPrivKey and encrypts it with the UnlockKey.
- During synchronization, the resulting copy (EncryptedRecoveryPrivKey) is sent to the Yandex server.
- As soon as the user syncs another device with the Yandex server, the EncryptedRecoveryPrivKey is sent to this device and stored there in encrypted form.
- When the user enters the master password (mPwd) on another device for the first time after syncing, the additional encryption is removed from the EncryptedRecoveryPrivKey. It is transformed to the RecoveryPrivKey, which is protected by the RecoveryUnlockKey.
- The RecoveryPrivKey is stored on the device and never synced in unencrypted form. By getting the RecoveryUnlockKey from the account, the user can reset the old master password and create a new one.
The key for encrypting the password store.
The master password. The user must remember it and enter it every time they need to access site passwords.
The public key. Used for encrypting EncKey. Stored in plain text (unencrypted) format.
Key (passphrase) used for encrypting PrivKey. The result of repeated hashes of the master password. It is computed each time the master password is entered.
Private key. Used for decrypting EncKey. It decrypts EncKey and user passwords, so it is protected by a passphrase. UnlockKey is used as the passphrase.
The key that encrypts RecoveryPrivKey. Stored in the Yandex account.
A copy of the RecoveryPrivKey private key for resetting the master password. It is encrypted using UnlockKey. It is sent to the server for syncing with other devices.
A copy of the private key that decrypts EncKey. Used for resetting the master password. Stored on the device in encrypted format and requires RecoveryUnlockKey for decryption. For transmission over the network, it is also encrypted with UnlockKey during syncing.